By industry
By initiatives
By industry
By initiatives
API Security | Dec 9, 2025 | 10 min read | By Savan Kharod

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
Are your APIs vulnerable to attacks that could compromise sensitive data? With 80% of web applications facing API security issues, understanding the OWASP API Security Top 10 is more crucial than ever.
This article will explore how AI can help you effectively combat these risks, providing actionable insights and real-world strategies to safeguard your applications.
The OWASP API Security Top 10 is a list of the most critical API security risks, maintained by the OWASP Foundation under the OWASP API Security Project. It highlights common vulnerabilities such as broken authorization, misconfigurations, and unsafe API consumption, aiming to help developers and security teams prioritize defenses across API ecosystems.
The list was first published in 2019 and updated in 2023 to reflect evolving threats, including new categories like Server-Side Request Forgery (SSRF) and Unsafe API Consumption. Attackers increasingly target APIs because they enable communication and data sharing between services, making robust API security essential.
[table]
AI plays a crucial role in modern API security by enhancing defenses against evolving threats. It automates vulnerability detection and monitors real-time traffic to identify anomalous behaviors that may signal attacks. This capability allows teams to respond swiftly and effectively to potential breaches.
AI-driven platforms can continuously scan APIs for OWASP Top 10 risks, simulating real-world attack scenarios to provide actionable insights for remediation. Traditional perimeter defenses often fall short for API threats; AI offers dynamic, context-aware protection that adapts to new attack techniques. Notably, a recent study reported a 32% increase in API attacks that exploit these OWASP risks.
Artificial intelligence plays a crucial role in enhancing API security by directly addressing specific risks outlined in the OWASP API Security Top 10. One significant advantage is the automation of discovering shadow and outdated endpoints. AI-powered tools not only monitor for real-time anomalies but also correlate vulnerabilities with their business impact, enabling teams to prioritize responses effectively.
Automated scanners and dynamic sensors further bolster security efforts. These tools validate exposure and prioritize remediation, mapping attack paths across data, identities, and workloads. This proactive approach helps organizations stay ahead of potential threats by identifying vulnerabilities before they can be exploited.
Moreover, AI can simulate attacker behavior, revealing weaknesses that static analysis methods often miss. This capability is vital because it enables teams to understand how an attacker might exploit vulnerabilities in real-world scenarios.
By employing these advanced techniques, organizations can enhance their defense mechanisms against risks such as Broken Object Level Authorization and Broken Authentication.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
BOLA occurs when APIs fail to verify if a user is authorized to access a specific object, leading to unauthorized data access and manipulation. This vulnerability can allow attackers to exploit sensitive data and perform actions beyond their intended permissions. AI can detect patterns of unauthorized access attempts, flag suspicious requests, and enforce fine-grained authorization rules in real time, significantly enhancing security.
Weak authentication mechanisms expose APIs to various threats. Common issues include weak passwords, lack of multi-factor authentication (MFA), poor session management, and exposed API keys. These vulnerabilities can lead to unauthorized access and data breaches.
AI can significantly enhance security by identifying threats such as credential stuffing, brute-force attacks, and session hijacking through analysis of login patterns and session anomalies. Implementing stronger authentication measures is essential for safeguarding API environments.
Excessive data exposure occurs when APIs inadvertently expose more data than necessary, increasing the risk of data leaks. This vulnerability can arise from overly broad response structures or insufficient filtering of sensitive information.
To mitigate this risk, AI can play a crucial role by monitoring API responses for sensitive data exposure. It can recommend data minimization strategies and enforce strict response schemas, ensuring that only essential information is shared. Implementing these practices helps maintain data privacy and strengthens overall API security.
Misconfigurations pose significant security risks in API environments. Misconfigured endpoints, default settings, and unnecessary features expand the attack surface. Attackers exploit these vulnerabilities to gain unauthorized access or disrupt services.
To mitigate these risks, implementing automated solutions is crucial. AI can automate configuration management, enforce secure defaults, and detect misconfigurations across environments. This proactive approach helps maintain security compliance and reduces human error.
Regular audits and updates are also essential to ensure configurations align with best practices, ultimately strengthening the API's defense against potential threats.
Mass assignment occurs when APIs allow clients to update object properties without proper filtering, leading to unauthorized changes. This vulnerability can expose sensitive data and compromise system integrity. AI can analyze request payloads for mass-assignment risks and enforce property-level validation, thereby enhancing security against potential exploitation.
Improper asset management can significantly compromise API security. Poor inventory and management of API endpoints can leave shadow or outdated APIs exposed. This creates vulnerabilities that attackers can exploit.
To mitigate these risks, organizations should leverage AI-driven discovery tools. These tools can map all API assets, flag unmanaged endpoints, and recommend deprecation or security controls.
By maintaining an accurate inventory and actively managing APIs, teams can enhance their security posture and reduce the likelihood of breaches. Proactive asset management is essential in today’s complex API environments.
Lack of rate limiting poses a significant threat to API security. Without it, attackers can exploit APIs, leading to denial-of-service or brute-force attacks.
This absence can result in system overloads, making services unavailable to legitimate users. Implementing AI can help mitigate these risks by dynamically adjusting rate limits based on traffic patterns.
It can also detect abnormal request spikes, allowing teams to respond swiftly to potential threats. By leveraging AI, organizations can enhance their API defenses and better control their traffic flow.
When you work through the OWASP API Top 10, you’ll find recurring themes: unusual traffic patterns, attacks hiding behind valid credentials, sensitive‑data leaks, unauthorized access, and blind spots in logging and monitoring. That’s where a strong observability and intelligence layer becomes indispensable.
Here’s how Treblle uses AI and runtime analytics to help you tackle those key risks, not just by telling you a vulnerability might exist, but by showing you real‑world traffic and behavior so you can prevent, detect, and respond.
Treblle continuously captures metadata on every API request, headers, payloads, parameter patterns, and status codes, then applies anomaly detection models to surface deviations from your typical “healthy” traffic.
For example, an unexpected spike in unauthorized status codes or repeated parameter‑value combinations can trigger an alert.
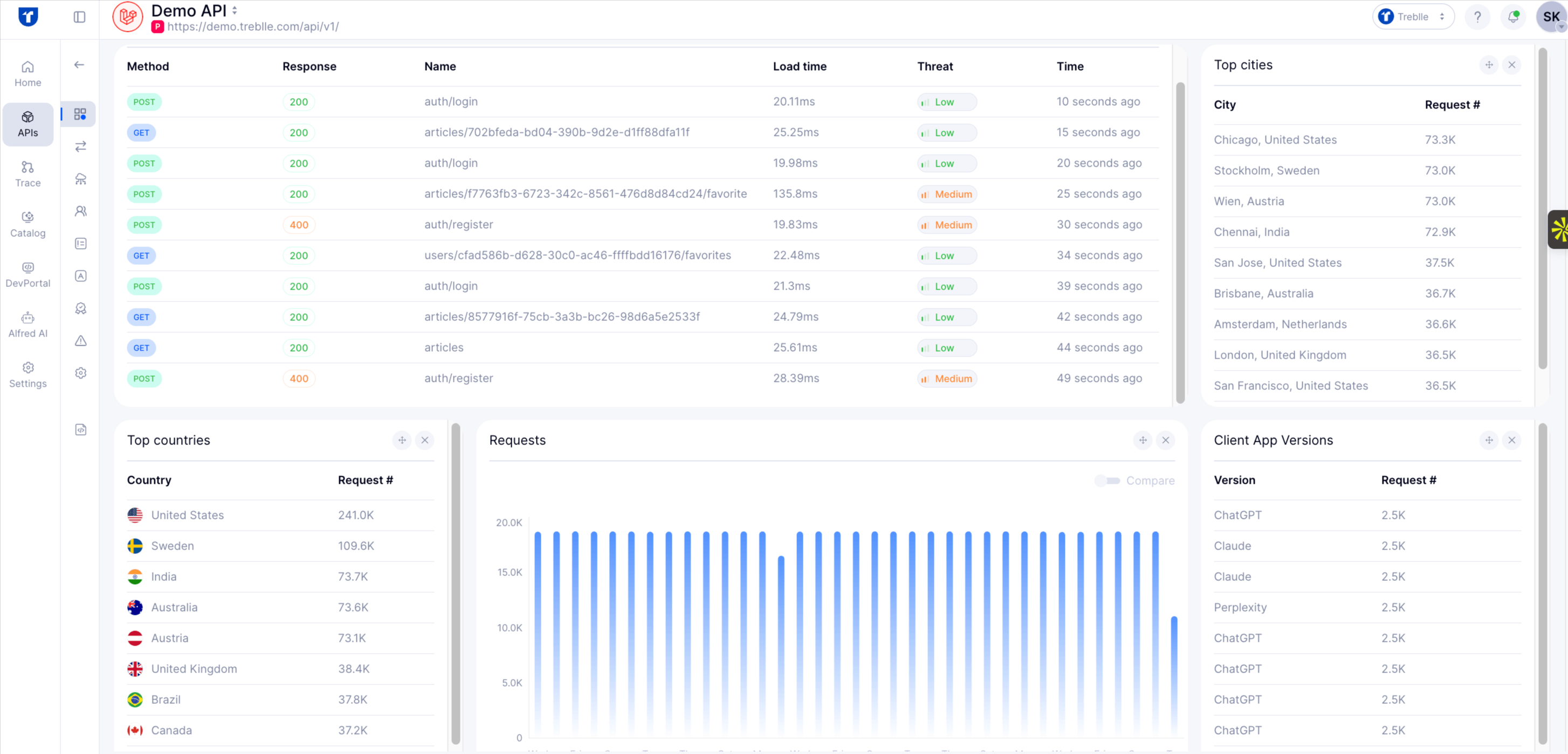
By doing this, Treblle helps you identify issues that map directly to OWASP risks, such as Broken Object Level Authorization (BOLA), Unrestricted Resource Access, and even Mass Assignment, because the system doesn’t simply look for known bad inputs; it learns what normal looks like and flags what’s abnormal.
One of the more complex parts of addressing API‑specific threats is gaining visibility into the exact parameters, objects, and endpoints your API processes. Treblle gives you a unified dashboard where you can see parameter usage across requests, track which fields show up, and identify unexpected fields or shapes.
This supports the evaluation of OWASP categories such as API1 - Broken Object Level Authorization, API4 - Lack of Resources & Rate Limiting, and API9 - Improper Inventory Management, because you can see whether unknown parameters or endpoints are being used, and you get context to ask why.
Regulated data exposure is one of the fastest‑moving targets for API security programs. Treblle’s SDKs and platform support field‑level masking: you configure which parameters or headers should always be redacted (e.g., card numbers, PII, social security values) before they are stored in logs or dashboards.
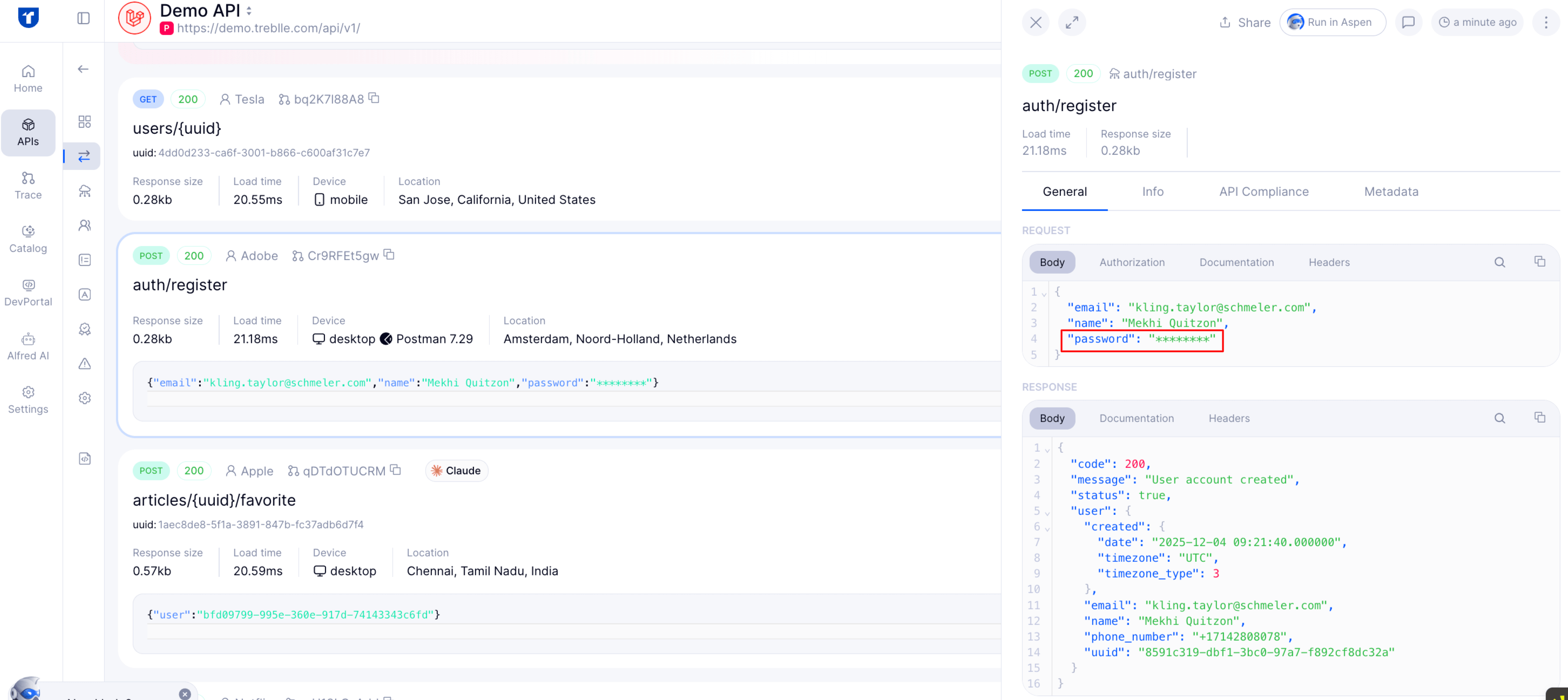
This capability helps you address risks such as API3 – Excessive Data Exposure, API6 – Mass Assignment, and API10 – Insufficient Logging & Monitoring, by ensuring that even your monitoring and observability layers don’t become another surface for sensitive data leakage.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protection doesn’t stop at collection and dashboarding. Treblle supports alerting for behavior that deviates from baseline, e.g., a new endpoint that receives many unexpected parameters, or a sudden increase in status‑403 errors across a user group. You can set custom alerts tied to parameter values, endpoints, response codes, and more.
These alerts directly support defence against OWASP risks like API2 - Broken User Authentication, API5 - Broken Function Level Authorization, and API8 - Injection, because they allow you to react to anomalous behavior rather than only known signatures.
AI-driven API security tools can enhance monitoring and threat detection, but they also come with limitations. These systems may generate false positives or miss novel attack patterns, making human oversight and regular updates essential. Relying solely on AI can create security gaps, as automated systems may not effectively interpret complex or evolving threats.
To maximize effectiveness, consider implementing these best practices:
Establish a robust feedback loop between AI tools and human analysts to refine detection algorithms continuously.
Regularly update and train AI models with new data to adapt to emerging threats.
Combine AI capabilities with traditional security measures for a layered defense.
Conduct routine audits to ensure compliance with security standards and identify potential vulnerabilities.
By following these guidelines, organizations can strengthen their API security posture while mitigating the inherent risks associated with automated tools. Balancing technology with human expertise is key to maintaining a secure API environment.
The future of API security is increasingly intertwined with advancements in AI and the established frameworks provided by OWASP. The integration of AI and OWASP API Security standards is transforming API protection, enabling proactive, adaptive defenses against evolving threats.
This shift allows organizations to identify vulnerabilities before they are exploited, enhancing their overall security posture.
As security practices evolve, continuous monitoring, automated remediation, and real-time observability are becoming industry standards for API security platforms like Treblle.
These capabilities streamline detection and response, reducing the window of exposure to potential attacks.
By leveraging AI for API security using tools like Treblle alongside OWASP guidelines, teams can better safeguard their APIs, ensuring compliance and resilience in a rapidly changing digital landscape.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityThree Chinese AI labs stole 16 million Claude interactions without triggering a single obvious alarm. They didn't hack anything. They just looked like regular users—until the numbers told a different story.
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.