API Security | Jun 10, 2025 | 12 min read | By Savan Kharod

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
Security might not be your top priority when building your first REST API,especially if you’re just getting started with a basic setup like creating a simple REST API with JSON. However, even in early development stages, it's crucial to implement basic authentication to prevent unauthorized access and potential abuse. An API key offers a straightforward method to control access, ensuring that only authorized clients can interact with your API.
Uncover why API security debt is the hidden cost of modern APIs, download The Anatomy of an API: 2025 Edition for free.
In this article, we will learn how to secure your first REST API with an API key, and I will also share some additional tips and best practices for securing your API key and REST API.
An API key is a unique alphanumeric string that serves as a simple form of authentication and authorization for applications interacting with APIs. It identifies the calling project or application, enabling API providers to control and monitor access to their services.
Key Characteristics
Now that we have refreshed our basics, let’s get into the details.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
API key authentication is a straightforward method to secure RESTful APIs, ensuring that only authorized applications can access your services. Here's a breakdown of how it functions:
When a client application registers to use your API, the server generates a unique API key—a long, random string that serves as a credential. This key is associated with the client's identity and permissions.
The client includes the API key in each API request, typically in the request header. This allows the server to identify and authenticate the source of the request.
Example using curl:
curl -H "x-api-key: YOUR_API_KEY" https://api.yourservice.com/endpointUpon receiving a request, the server checks the provided API key against its database:
If the API key passes all checks, the server processes the request. Otherwise, it responds with an appropriate error message, such as 401 Unauthorized. To improve your API’s resilience and clarity, follow these best practices for REST API error handling.
API keys enable you to implement fine-grained access control:
By associating API keys with specific clients, you can track usage patterns and detect anomalies, enhancing security and performance.
While API keys are easy to implement, they come with security considerations:
We will discuss the security considerations in detail later in this article. But for a brief overview, it's also advisable to restrict API keys to specific IP addresses or referrer URLs when possible, which adds an extra layer of security.
Before your API can authenticate clients, you need a unique, hard-to-guess token and a secure place to keep it.
.env file at your project root:API_KEY=your_generated_api_key.env to your .gitignore to prevent commits of sensitive data..env.example with placeholder values for onboarding.You’ll use dotenvto load your API key into process.env without hard-coding secrets.
Install the package
npm install dotenvThis adds the ability to read .env files in development
Load environment variables
At the very top of your entry file (app.js or index.js), add:
require('dotenv').config();Now process.env.API_KEY holds your key; no extra parsing needed
Encapsulate your authentication logic in middleware so it’s reusable and maintainable.
Read the x-api-key header
Fetch the key from req.headers['x-api-key'] in your middleware function.
Compare to the stored key
Check if the provided key matches process.env.API_KEY; return 401 Unauthorized if it doesn’t
// middleware/apiKeyAuth.js
module.exports = function (req, res, next) {
const clientKey = req.headers['x-api-key'];
if (!clientKey || clientKey !== process.env.API_KEY) {
return res.status(401).json({ error: 'Unauthorized' });
}
next();
};x-api-key header from each requestprocess.env.API_KEYHTTP 401Decide whether to lock down all endpoints or only specific ones. When designing your routes, refer to this REST API endpoint design guide to follow naming conventions and structure them effectively for future scalability.
Global Protection
const express = require('express');
const apiKeyAuth = require('./middleware/apiKeyAuth');
const app = express();
app.use(apiKeyAuth); // All routes now require a valid API key
app.get('/data', (req, res) => {
res.json({ message: 'Secure data' });
});Route-Specific Protection
app.get('/public', (req, res) => {
res.send('This is open to everyone');
});
app.get('/private', apiKeyAuth, (req, res) => {
res.json({ message: 'Protected data' });
});Use Aspen, Treblle's API testing tool to verify your API and ensure your API behaves as expected for both authorized and unauthorized requests:
# With valid key
curl -H "x-api-key: $API_KEY" http://localhost:3000/data
# Missing or invalid key
curl http://localhost:3000/data
# → 401 UnauthorizedAlways serve your API over HTTPS to protect the API key (and other credentials) in transit. Plain HTTP leaves keys vulnerable to interception.
To further harden your API:
express-rate-limit)In this section, you’ll learn the best practices for sending API keys with each request, ensuring secure transport via HTTP headers, seeing concrete examples in Aspen, and understanding common pitfalls to avoid.
Most REST APIs expect API keys in a custom header (e.g., x-api-key) or in the standard Authorization header with a scheme like Bearer. Custom headers keep your authentication method explicit and separate from other token types.
Using the Authorization: Bearer YOUR_API_KEY pattern aligns your API key usage with OAuth-style tokens, simplifying integration when you later adopt JWTs or OAuth2.
Headers are never logged in URLs by default and aren’t stored in browser history, reducing accidental exposure. Query parameters, in contrast, appear in access logs and can be cached by intermediaries, making them a known security risk for API keys.
Aspen is a free, zero-trust, native macOS HTTP client from Treblle, designed for rapid REST API testing with AI-powered assistance. And here’s why it might become your favorite API tool.
x-api-key and Value. Click Save, and head back to Aspen’s home screen.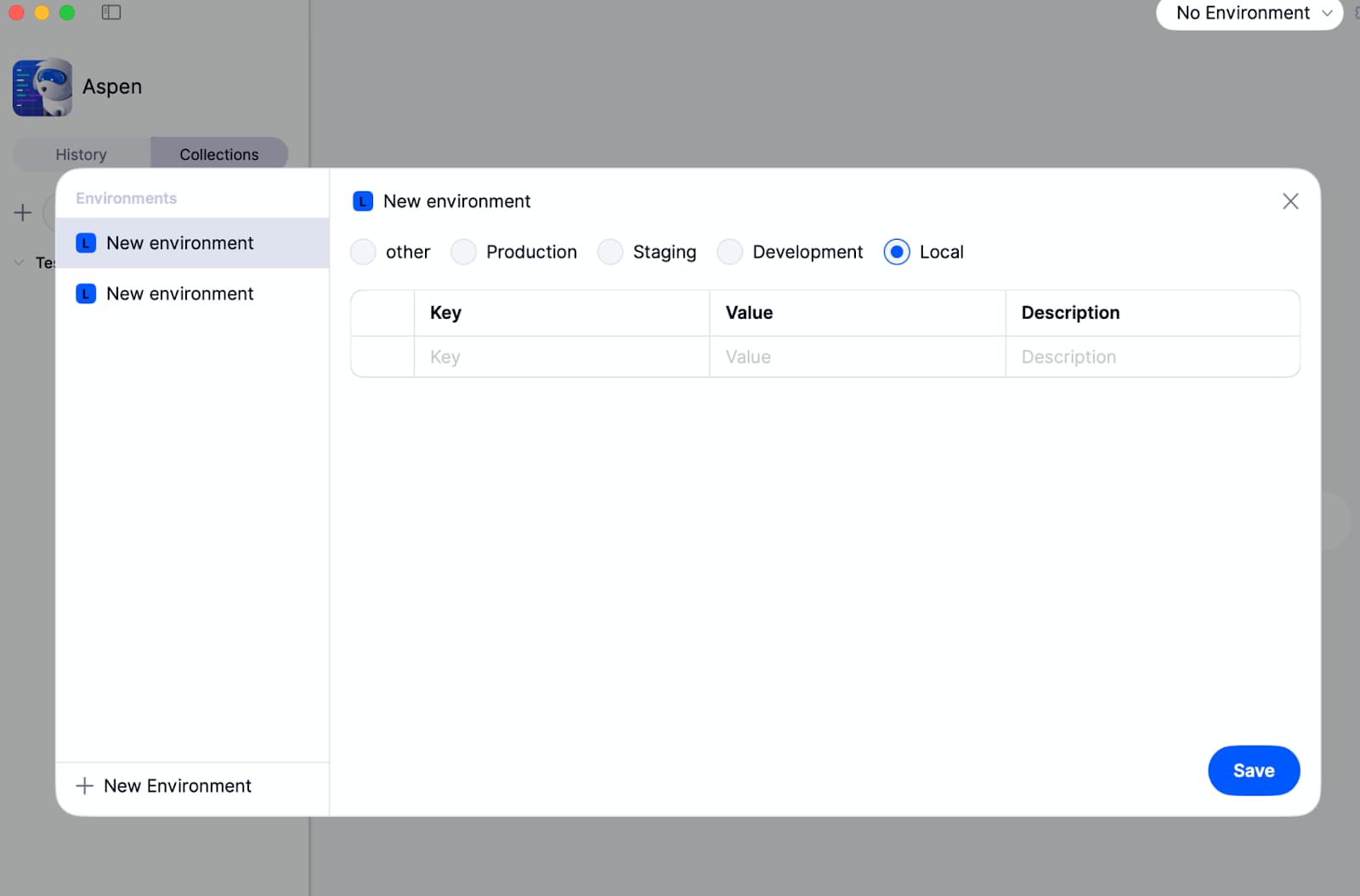
GET, POST, PUT, DELETE—check out this guide on HTTP methods for REST APIs to ensure you’re following conventions.401 Unauthorized error.API keys are critical credentials that grant access to your services. Proper management ensures security and prevents unauthorized access.
Create API keys using cryptographically secure random generators. Avoid predictable patterns to reduce the risk of brute-force attacks.
Never hard-code API keys into your application's source code. Instead, store them in environment variables or use a dedicated secrets management service.
Implement a key rotation policy to minimize the impact of a compromised key. Regular rotation limits the window of opportunity for misuse.
Apply the principle of least privilege by assigning only necessary permissions to each API key. This limits potential damage if a key is compromised.
Track API key usage to detect unusual patterns that may indicate misuse. Implement rate limiting to prevent abuse and ensure fair usage.
Do not expose API keys in client-side code, such as JavaScript or mobile applications. Instead, route requests through a secure backend server.
Ensure all API requests are made over HTTPS to encrypt data in transit, protecting API keys from interception.
Restrict API key usage to specific IP addresses, referrer URLs, or applications. This adds a layer of security by limiting where keys can be used.
Regularly audit your API keys and deactivate any that are no longer in use. This reduces the attack surface and prevents unauthorized access through forgotten keys.
Ensure all team members understand the importance of API key security and follow best practices to prevent accidental exposure.
While API keys are a straightforward method for authenticating applications, they have several limitations that developers should be aware of:
API keys authenticate the calling application, not individual users. This means:
For user-level authentication and authorization, protocols like OAuth 2.0 are more appropriate.
API keys typically do not expire automatically, and revoking them requires manual intervention. This poses risks:
Implementing key rotation and expiration requires additional infrastructure and processes.
API keys often grant broad access to the API, lacking fine-grained control:
Advanced authorization frameworks like OAuth 2.0 provide scopes and roles to manage access more precisely.
Systems transmit API keys in plaintext unless developers implement additional security measures such as:
Always use HTTPS to encrypt API requests and responses, ensuring the confidentiality and integrity of the data.
API keys can be inadvertently exposed through:
To mitigate these risks:
Implementing API key authentication is a crucial first step in securing your REST API. It provides a straightforward method to control access and monitor usage. However, as your application scales and security needs evolve, it's essential to consider more robust authentication mechanisms like OAuth 2.0 or JWTs.
For developers seeking an efficient and privacy-focused tool to test and manage their APIs, Aspen by Treblle offers a compelling solution. Aspen is a free, native macOS application explicitly designed for REST API testing. It requires no login, ensuring your data remains local and secure. With its AI-powered assistant, Alfred, Aspen can generate data models, OpenAPI specifications, and integration code, streamlining your development workflow.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.