By industry
By initiatives
By industry
By initiatives
API Security | May 19, 2025 | 6 min read | By Rahul Khinchi

Rahul Khinchi is a Developer Advocate at Treblle, where he focuses on improving API workflows and developer experience. He writes technical content on API observability, security, and governance, and builds open-source tools to demonstrate real-world API use cases. Rahul has spoken at developer meetups and universities, and previously held developer advocacy roles at Syncloop. He was selected for Google Summer of Code in 2022 and has led community initiatives supporting thousands of beginners in open source.
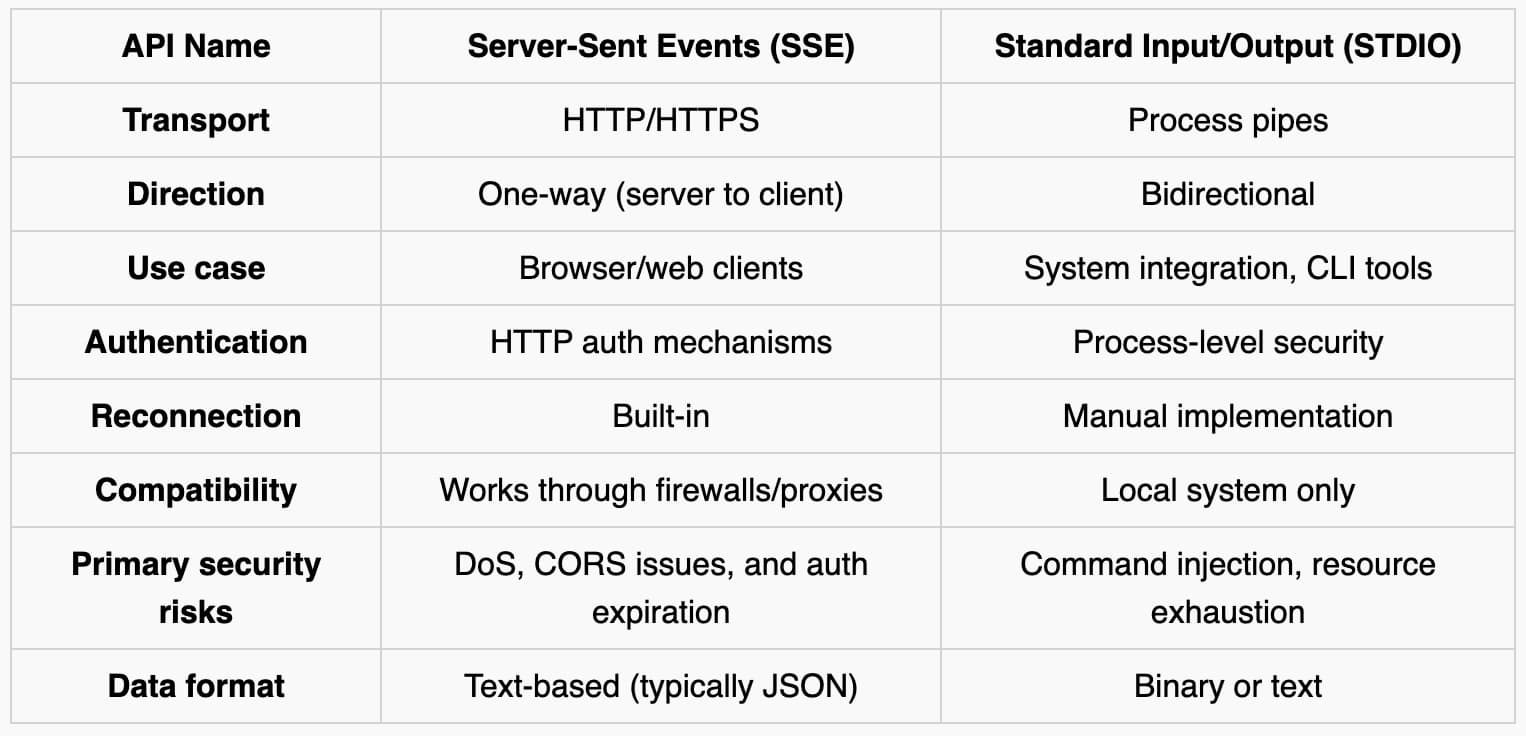
You’ve likely built an API that needs to push data to clients in real-time. Whether you’re streaming logs, sending notifications, or updating dashboards without refreshing, you’ll encounter two approaches: Server-Sent Events (SSE) and Standard Input/Output (STDIO) streaming.
Both solve real-time communication problems but have distinct security considerations. Let’s examine their technical nuances and security implications.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Server-sent events (SSE) are a web technology in which a server pushes client updates over a single HTTP connection. Unlike WebSockets, SSE provides one-way communication from server to client, making it ideal for scenarios like live dashboards or notifications.
With SSE, browsers maintain an open connection to the server, which sends new data as it becomes available. No repeated client requests are needed.
Standard Input/Output (STDIO) refers to the standard streams (stdin, stdout, stderr) used for input/output operations in operating systems. In web development, STDIO patterns often involve processes communicating through these streams, such as spawning child processes or executing system commands.
SSE connections can stay open indefinitely (like a Zoom meeting no one remembers to end), raising token expiration challenges. If a token expires mid-connection, attackers could hijack the session.
Solution: Implement token refresh callbacks. Think of it as a digital bouncer checking IDs at the door:
// Client refreshes token and reconnects when needed
eventSource.addEventListener('token-expiring', (event) => {
eventSource.close();
refreshToken().then(() => {
// Reconnect with new token
connectToEventSource();
});SSE follows CORS policies. If your API serves multiple origins, you'll need proper CORS headers:
res.writeHead(200, {
'Content-Type': 'text/event-stream',
'Cache-Control': 'no-cache',
'Connection': 'keep-alive',
'Access-Control-Allow-Origin': 'https://trusted-origin.com'
});Be careful with wildcards (*). They open your stream to any origin.
Without rate limiting, SSE endpoints can become DoS vectors. An attacker could establish many connections, overwhelming your server.
Solution: Use middleware to cap active streams:
// Simple connection counter middleware
function limitConnections(req, res, next) {
if (activeConnections >= MAX_CONNECTIONS) {
return res.status(429).send('Too many connections');
}
activeConnections++;
req.on('close', () => activeConnections--);
next();
}SSE runs over HTTP(S). Always use HTTPS to prevent traffic interception.
Unlike WebSockets, SSE has no separate protocol (ws:// or wss://). Instead, it uses the standard https:// protocol, reducing confusion about whether your connection is secure.
Passing unsanitized input to child processes is like letting strangers type sudo commands on your terminal while you’re AFK.
This vulnerable code accepts user input directly into a command:
// VULNERABLE CODE - DO NOT USE
const userInput = req.query.filename;
const child = spawn('cat', [userInput]);Your server after running this:
Secure Alternative:
const allowedFiles = ['log1.txt', 'log2.txt', 'log3.txt'];
const userInput = req.query.filename;
if (!allowedFiles.includes(userInput)) {
return res.status(400).send('Invalid file');
}
const child = spawn('cat', [userInput]);Child processes consume system resources. An attacker might try to spawn many processes to exhaust your server's capacity.
Implement safeguards:
let activeProcesses = 0;
const MAX_PROCESSES = 10;
function spawnSafeProcess(command, args) {
if (activeProcesses >= MAX_PROCESSES) {
throw new Error('Too many processes');
}
activeProcesses++;
const child = spawn(command, args);
child.on('exit', () => {
activeProcesses--;
});
return child;
}STDIO streams buffer data. Without proper handling, large outputs can consume excessive memory.
// Set limits on stdout data
const child = spawn('some-command');
let dataSize = 0;
const MAX_SIZE = 10 * 1024 * 1024; // 10MB
child.stdout.on('data', (data) => {
dataSize += data.length;
if (dataSize > MAX_SIZE) {
child.kill('SIGTERM');
throw new Error('Output too large');
}
// Process data
});When working with file-based STDIO operations, path traversal attacks are a risk:
// VULNERABLE CODE - DO NOT USE
const logFile = `./logs/${req.params.date}.log`;
const tailProcess = spawn('tail', ['-f', logFile]);A request with ../../../etc/passwd as the date parameter could expose sensitive files.
In mid-2024, researchers discovered a critical vulnerability (CVE-2024-4577) in PHP running on Windows in CGI mode. The issue? PHP improperly parsed special Unicode characters passed via HTTP requests, due to Windows’ "Best-Fit" character encoding, which allowed attackers to inject command-line arguments.
This incident wasn’t just theoretical. Exploits in the wild deployed malware like Gh0st RAT and crypto miners by injecting commands directly via STDIO.
Example:
php-cgi.exe -r "please_dont_bitcoin_mine_on_my_db_server" A perfect horror story for your next security standup.
This flaw showed how assumptions around input encoding and STDIO handling can open the door to complete remote code execution.
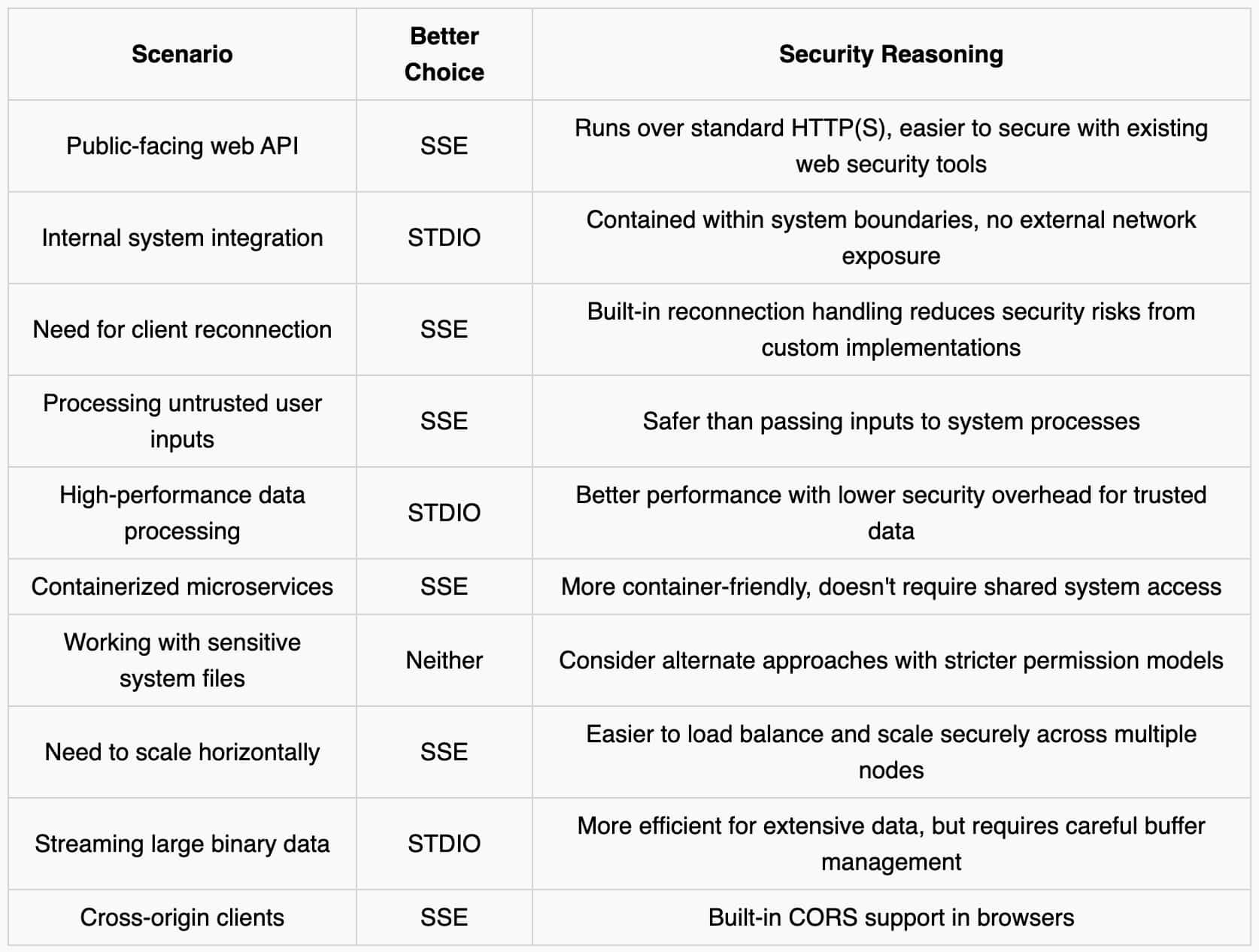
To help you make the right security decision for your specific use case, here's a decision matrix that outlines when each approach makes the most sense from a security perspective:
Track these metrics unless you enjoy debugging incidents that start with “But it worked in my local Docker container!”:
For SSE, use tools like Treblle’s API Observability to detect anomalies.
SSE and STDIO offer distinct paths to real-time functionality—but each comes with tradeoffs that go well beyond performance or convenience. SSE shines for lightweight, browser-compatible, one-way communication, but it demands constant vigilance around authentication longevity, connection abuse, and CORS exposure.
Meanwhile, STDIO offers power and flexibility for deeper system-level integrations—but it’s a favorite playground for attackers exploiting unsanitized inputs, process overload, and path traversal vulnerabilities.
Security isn’t just about patching obvious holes—it’s about recognizing how easily a helpful feature becomes an attack vector. The same connection that updates your dashboard could be the entry point for session hijacking. That helpful CLI interface might give someone shell access if you’re not cautious.
So before you ship:
And if you’re in doubt?
Favor simplicity with transparency over complexity with caveats.
Because in real-time systems, a few missed safeguards don’t just slow things down—they open doors you didn’t mean to unlock.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityThree Chinese AI labs stole 16 million Claude interactions without triggering a single obvious alarm. They didn't hack anything. They just looked like regular users—until the numbers told a different story.
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.