By industry
By initiatives
By industry
By initiatives
API Design | Mar 7, 2023 | 7 min read | By Davor Kolenc

Davor Kolenc is a growth and content marketer, specializing in API observability and monitoring. He crafts developer-focused narratives and strategic content, regularly sharing insights through blog posts on IndieHackers, Hacker News, Dev.to, and Medium. Davor also engages with the developer community via social platforms like X, LinkedIn, Hacker Noon, and Product Hunt. His work centers on delivering meaningful value to software teams through content-driven growth and practical API guidance.
APIs (Application Programming Interfaces) have been crucial for businesses to facilitate distributed systems. They help organizations build a decoupled architecture using different services, all communicating through APIs. Not just services, APIs can connect different systems and applications, allowing them to communicate with each other.
APIs facilitate data sharing between heterogeneous systems where hackers try to attack. Cyber attackers target APIs to access systems using them as entry points. API security breaches can lead to data theft, financial fraud, and malicious activities.
According to a survey, 41% of organizations faced an API security incident leading to a data breach in 2021. So, API security becomes crucial for businesses to ensure a secure customer experience.
Here we will discuss API security, how to deal with different threats to APIs and best practices for handling them.
API security is a set of processes and practices organizations use to protect their systems from unauthorized access and misuse. It includes authentication, authorization, and encryption mechanisms to control access and protect data integrity.
So, security becomes crucial if you use a distributed system with several services communicating through APIs. Let’s first understand what an API is briefly.
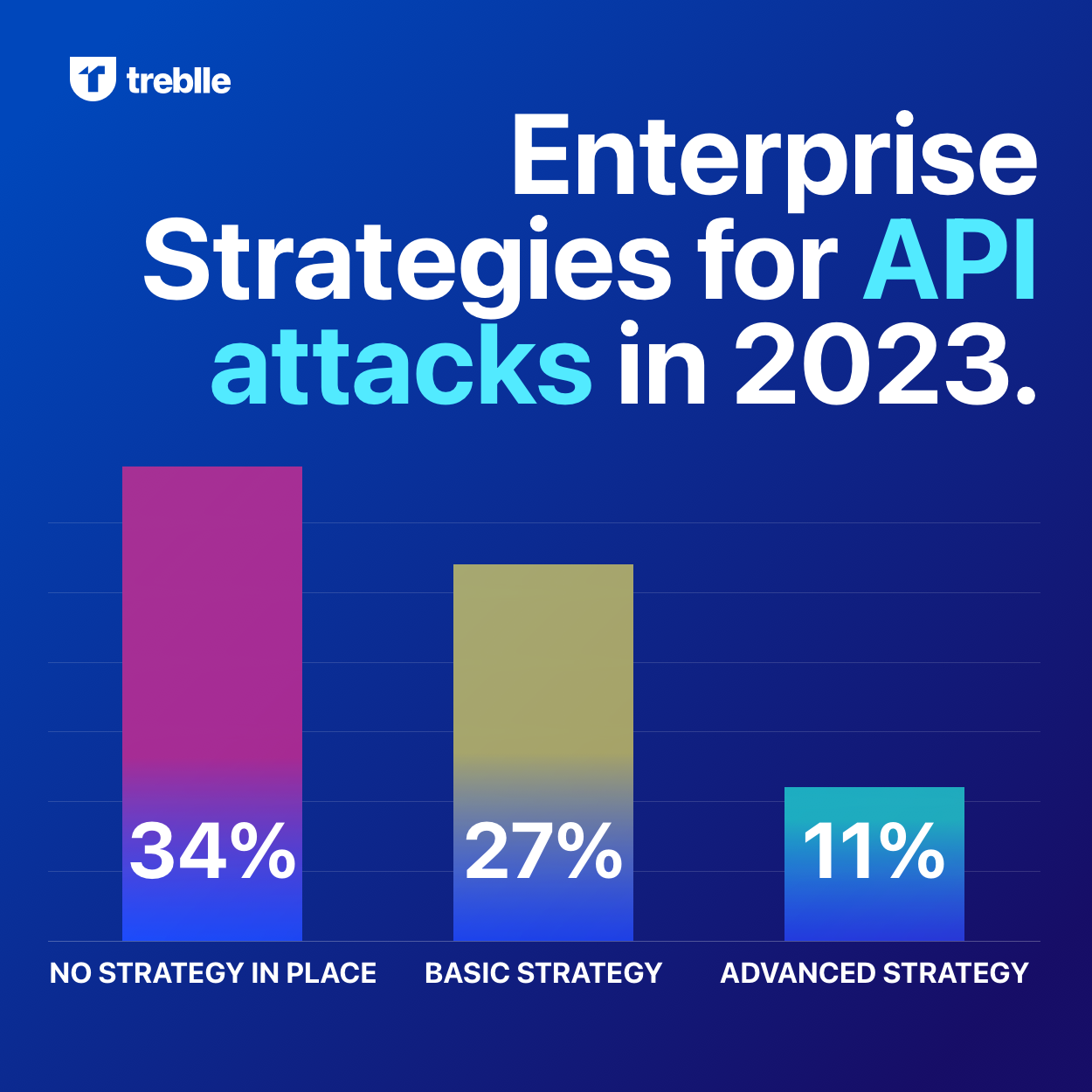
API security is the practice of protecting your APIs from unauthorized access. Systems communicate with each other through APIs, and that is why it becomes crucial to secure them. One of the most common cyber threats APIs experience is malicious code injections.
Due to malicious code executions triggered through system activity or a user request, hackers can access sensitive information. Let’s understand how exactly hackers attack your APIs.
One common way cyber attackers can access a secure API is by compromising the authentication mechanisms. This is a significant API security threat, where attackers access user information stored in the system.
Another significant API security threat is cross-site scripting (XSS), where an attacker injects malicious code into a web page. When these users access the page, the code in question executes automatically. It can take unexpected actions on their behalf, such as running unwanted scripts or stealing information from their browsers.
Many organizations deploy various security measures to protect APIs from unauthorized access. These include restricting user access to specific functions within an API, implementing authentication mechanisms, and monitoring for malicious activity targeting the API.
However, XSS is not the only API security threat; there are many others, like
An injection attack is one of the most common API security threats. Cyber attackers use it to gain unauthorized access to protected APIs. With an injection attack, an attacker tricks a user into entering malicious code directly into the API interface.
This can be done in several ways, including
One of the most common ways attackers access secure APIs is through broken authentication and authorization. An attacker uses social engineering practices to gain vital user credentials.
Then, attackers use these credentials to impersonate authorized users within the system. This gives them unrestricted access to resources owned by that particular user and potentially sensitive information stored on behalf of other users in that organization.
A DoS attack disrupts the functionality of a system or network by flooding it with requests that are too large for the resources to handle. A common type of DoS attack is called Request Forgery (RF). In RF attacks, attackers use social engineering to trick users and place a request to access secure systems on their behalf.
This request then overloads the server and prevents legitimate requests from being handled. Due to the flooding of requests, application performance degrades for all users who try to access the affected resource.
Now that we know your systems' threats, here are some API security best practices to follow.
Verifying user credentials before allowing them access to specific functions within an API is a fundamental API security best practice to follow. However, many other best practices exist, like implementing session management policies, developing a framework, or establishing authentication mechanisms to secure apps.
An API security threat model helps understand how potential security threats may affect your systems. It provides a framework for anticipating and understanding how attacks might attempt to exploit vulnerabilities, ultimately affecting infrastructure, products, processes, and people.
The API security threat model allows organizations to analyze their exposure to attacks targeting APIs. Further, it helps ensure appropriate measures are in place to protect themselves from these risks.
The following are some common elements that could be included in the API security threat model:
Data authentication and authorization are critical to ensure that data access privileges are not abused. You can leverage multi-factor authentications to ensure user credentials are not misused.
For example, you can use two-factor authentication for API security. Users with access privileges to internal and external APIs should be asked to use two-factor authentication. In two-factor authentication, users must provide their credentials with a passcode or one-click sign-in through a message delivered on a personal device.
You can use encryptions to ensure API security. The best way to encrypt APIs is to use code-signing certificates. You can get a code signing certificate from the certificate authority (CA) by submitting a certificate signing request (CSR).
Once submitted, CA validates the information in CSR and issues the certificate you can install on applications to secure APIs.
Input validation checks whether incoming data is appropriately formatted. At the same time, output encoding ensures that the information sent from an API is safe to display publicly.
For example, if an API sends the user name and password information in plaintext form, it can be a cybersecurity risk. Attackers can exploit user credentials and access sensitive data. Encoding this data will make it difficult for someone to decode and use this sensitive information.
Rate limiting is an API security best practice where you can limit the number of requests an individual user can make per minute. This prevents an attacker from abusing the API to flood it with traffic, causing the system to become congested.
It also helps to prevent unwanted automated actions from being carried out. Take the example of an eCommerce application exposing an API for users to place orders, check order status, and perform other actions. You can implement rate limiting to restrict the number of requests a user can make within a specific time period to prevent API abuse.
As the API ecosystem continues to grow and evolve, API security will likely remain a priority for organizations. As more companies develop their APIs, protecting them from unauthorized access becomes even more critical.
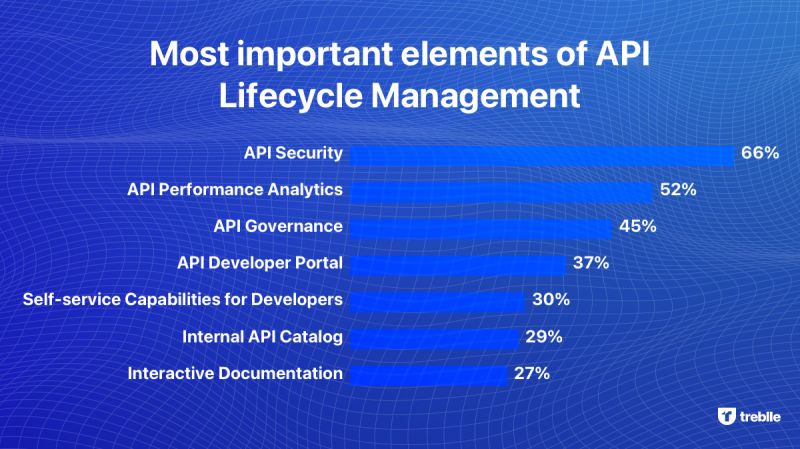
In addition, continued technological advances will make it easier for attackers to exploit vulnerabilities in APIs. 5G connectivity is a fine example of how improved technology can challenge API security. With improved networks and faster connectivity, IoT devices will need enhanced API security.
If IoT API is not secure, attackers can access the networks and sensitive information. This is why having an API security threat model becomes crucial to ensure advanced visibility and plan your cybersecurity measures accordingly.
API security is one of the most important aspects of data protection. Understanding and mitigating API threats can help protect your data from cyberattacks. This blog has outlined some of the most common threats and how to protect your systems using API security best practices. However, which best practice to use depends on specific business needs.
So, it is crucial to analyze your applications and business requirements to design an API security threat model.
 API Design
API DesignDiscover the 13 best OpenAPI documentation tools for 2026. Compare top platforms like Treblle, Swagger, and Redocly to improve your DX, eliminate documentation drift, and automate your API reference.
 API Design
API DesignAPI authorization defines what an authenticated user or client can do inside your system. This guide explains authorization vs authentication, breaks down RBAC, ABAC, and OAuth scopes, and shows how to implement simple, reliable access control in REST APIs without cluttering your codebase.
 API Design
API DesignRate limiting sets hard caps on how many requests a client can make; throttling shapes how fast requests are processed. This guide defines both, shows when to use each, and covers best practices.