Other | Jul 28, 2025 | 4 min read | By Savan Kharod | Reviewed by David Blažević

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
On June 26, 2025, we hosted the ‘What Really Breaks API Security’ webinar with API Security expert Colin Domoney and Vedran Cindrić, moderated by Harsha Chelle.
Together, they explored real-world API breaches, uncovered common mistakes, and shared developer-friendly strategies to harden APIs against modern threats.
In this summary article, you will learn:
How and why API security failures happen
Debunked myths around cloud security
A practical checklist to harden your APIs
Emerging threats from AI and new protocols
Recommendations to continuously protect against evolving risks
Want the full deep dive? Download the ebook Colin Domoney wrote after the webinar to explore everything that breaks in API security—and how to fix it.
Colin walked us through critical misconfigurations he encountered in his career, such as deficient rate limiting, exposed debug endpoints, and missing auth enforcement.
Colin shared a breach where a forgotten endpoint, left unauthenticated, exposed sensitive data publicly. He quoted and added:
“It was a simple misconfiguration, but it led to a complete data leak, no patch, no expiry, just open to the world.”
The key takeaway? Even the most basic lapses can have catastrophic consequences. So, remember to audit all endpoints, as security isn’t just about tools; it’s about maintaining configuration discipline.
“Most teams believe their APIs are secure, until something breaks.” - Vedran.
Vedran emphasized that relying on authentication alone creates a false sense of security. He explained that authentication is only one layer of security. True security means:
Authorization: Enforce least-privilege roles in your RBAC policies.
Input validation: Use JSON Schema or OpenAPI validators to reject malformed payloads.
Runtime observability: Monitor anomalies, not just auth failures.
Next, Harsha, Vedran, and Colin discussed the importance of having security checks in the CI/CD pipeline to catch issues before they become breaches.
Here’s a summarized checklist:
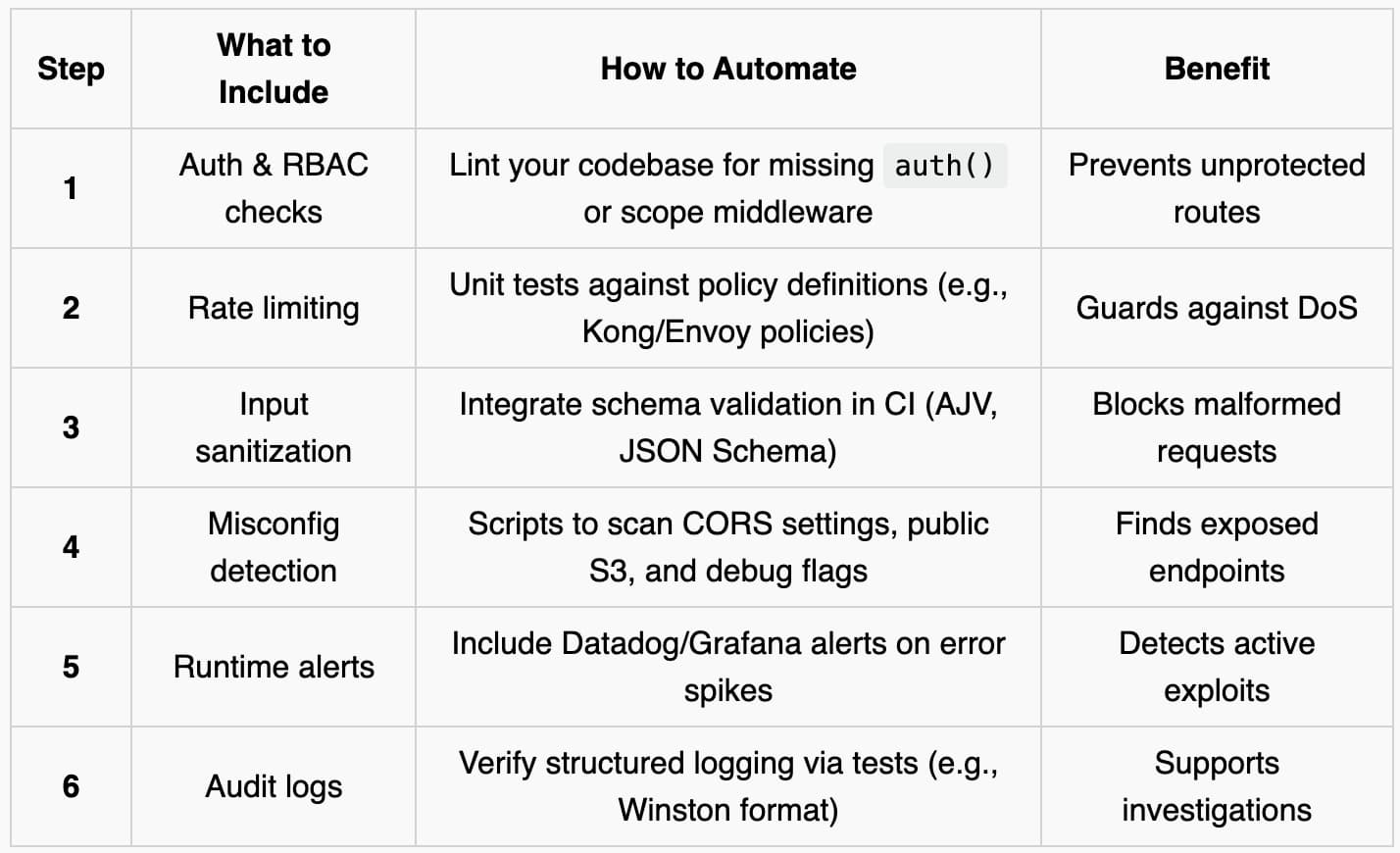
By codifying these checks in your build and using tools like ESLint, GitHub Actions, or Jenkins pipelines, you shift security “left” and catch issues before they are merged.
New to securing REST APIs? Start with this guide to securing your first REST API for a hands-on walkthrough.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
“With AI agents and protocols like MCP, the API attack surface has grown again.” - Colin Domoney
Colin highlighted two fast-evolving fronts:
AI-driven scraping: Bots can now automatically probe thousands of endpoints.
Model Context Protocol (MCP): New metadata channels that, if unguarded, expose business logic via context queries.
Colin then explained that mitigating these threats requires vigilance beyond static defenses. He mentioned implementing the following:
Behavioral baselining: Utilize anomaly-detection libraries to identify and flag non-human traffic patterns.
Scoped tokens: Issue short-lived, context-limited API keys for AI agents.
Entropy-based throttling: Rate-limit per token fingerprint, not just IP.
“Security demands more than checklists and hope.” - Colin Domoney
Colin highlighted that security must be continuous, not periodic. Weekly config scans, canary rollout pipelines, real-time dashboards, and blameless incident reviews are all part of the modern DevSecOps cycle.
Not sure what tools to start with? Explore our top picks for API security tooling in 2025.
Just before closing off the webinar, Colin shared the simple, 5-step playbook that anyone can implement to secure their APIs from conventional and modern malicious actors:
Map your APIs
Embrace Shift-left
Leverage your gateways
Test, test, and test
Use standard patterns and frameworks.
API security is not a checkbox; it’s a developer-embedded discipline that must adapt as infrastructure and threats evolve. As Colin Domoney emphasized:
“In 2025, API security demands more than checklists and hope.”
This encapsulates the core message of the webinar: surface-level measures often fail, and true security requires embedding guardrails at every layer, from CI/CD to runtime.
By regularly auditing environments for authentication and misconfiguration issues, automating schema validation, throttling, and configuration scans in pipelines, and evolving through continuous feedback loops, canary releases, and security retrospectives, you can transition API security from reactive firefighting to proactive resilience.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 Other
OtherHackers breached FIA’s driver portal, exposing Max Verstappen and other F1 drivers’ data. In this article, we covered a detail breakdown, security takeaways, and how it could have been stopped.
 Other
OtherIn Sept 25, JLR suffered a major cyber attack. In this article, we provided a complete breakdown of the JLR breach, detailing what happened, how it occurred, and the lessons learned.
 Other
OtherThe newly developed Treblle Next.js SDK supports the App Router, Pages Router, and Edge runtime.