API Security | Jan 13, 2025 | 10 min read | By Savan Kharod | Reviewed by Vedran Cindrić

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
• Postman data leak exposed over 30,000 public workspaces, revealing sensitive information like API keys, tokens, and credentials due to misconfigured sharing settings.
• Poor security practices, including inadequate secrets management, failure to rotate API keys, and insufficient training, were the main causes.
• The leak allowed attackers to exploit leaked credentials, leading to unauthorized API access and potential data theft.
• To prevent similar incidents, teams should adopt stricter access controls, use secrets management tools, rotate API keys regularly, and train developers on secure API practices.
Uncover why API security debt is the hidden cost of modern APIs, download The Anatomy of an API: 2025 Edition for free.
On December 23, 2024, CloudSEK's TRIAD team unveiled a critical security issue involving Postman, a widely used API development and testing platform. Their investigation revealed over 30,000 public workspaces leaking sensitive information such as API keys, access tokens, and refresh tokens.
These misconfigurations exposed businesses and individuals to significant risks, including unauthorized access to cloud resources, payment gateways, and third-party services.
The problem stemmed from improper workspace settings, insufficient use of secrets management tools, and a lack of API key rotation. Despite the widespread use of Postman, many developers failed to follow basic security protocols, highlighting the urgent need for stricter access controls and better education about secure API practices.
Let’s examine the technical details and root causes of the Postman data leak to understand the severity of this breach.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
The Postman data leak exposed over 30,000 workspaces, revealing sensitive information such as API keys, tokens, and administrator credentials. api.github.com, slack.com, login.microsoft.com, and salesforce.com were some of the major platforms affected by the breach:
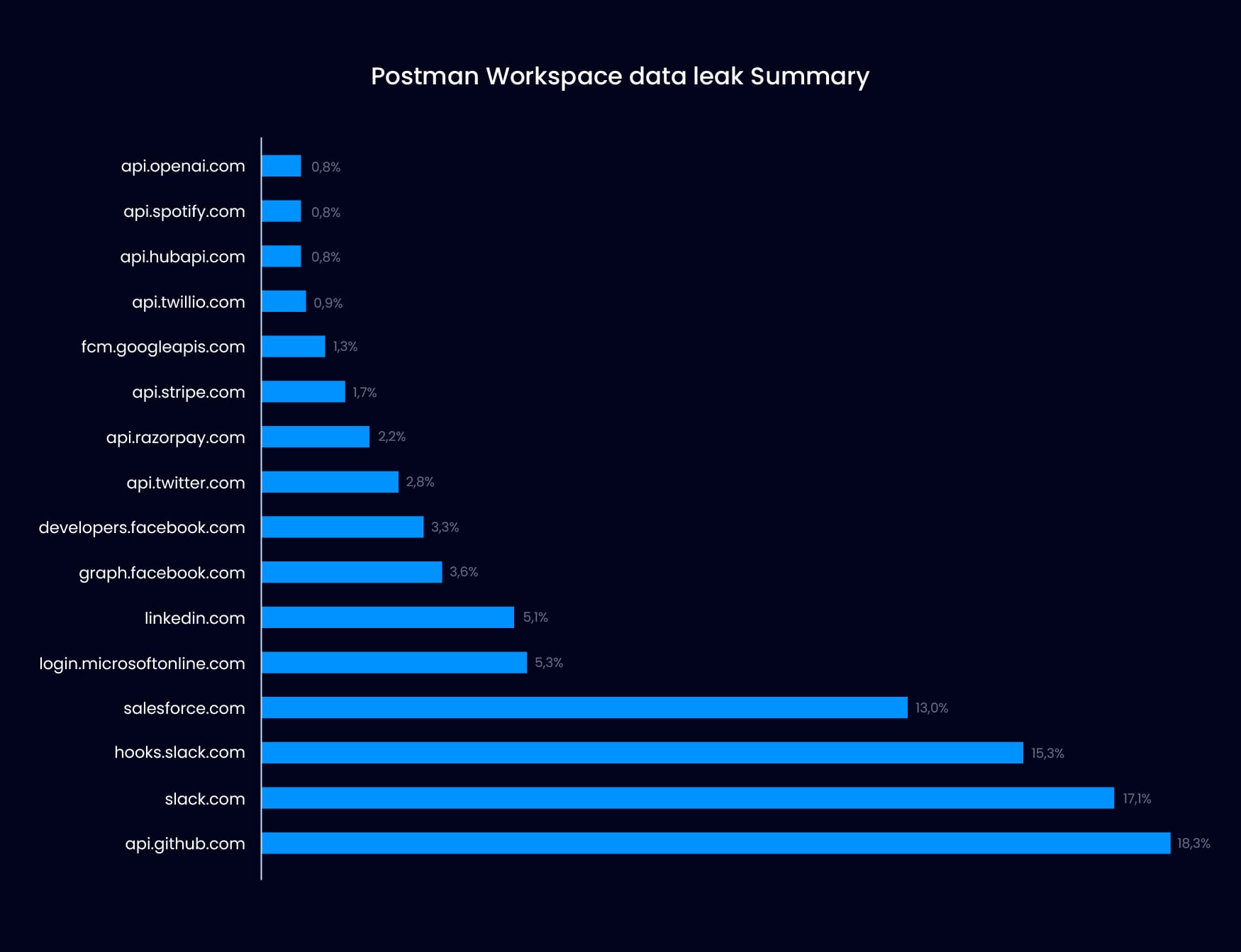
Summary of Postman's data leak
The root cause of the breach was the improper use of Postman’s sharing and collaboration features, coupled with insufficient security practices. Here’s a closer look at the technical details:
Postman workspaces are designed to facilitate collaboration, enabling teams to share environments, collections, and variables. However, misconfigured visibility settings led to many workspaces being set to “public” rather than “private.”
An attacker finding an exposed workspace URL could extract credentials and use them to make unauthorized API requests, access sensitive data, or manipulate systems connected to the API.
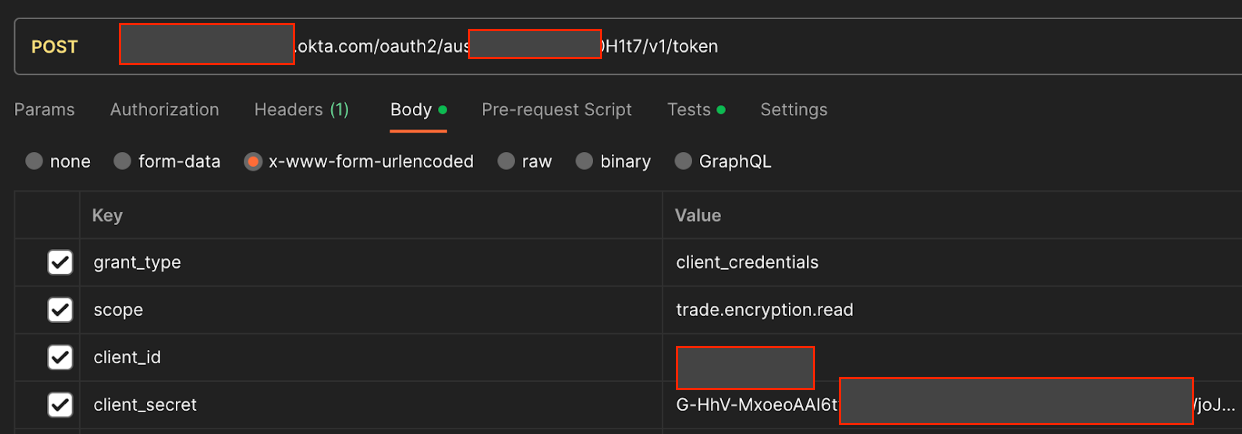
Snapshot of leaked credentials in Postman API breach
Many Postman users stored sensitive credentials directly within environment variables, ignoring or underutilizing the tool's built-in security features, such as secret management.
Organizations often fail to rotate exposed API keys promptly, exacerbating the problem.
One of the most significant contributors to the Postman API breach was a lack of awareness among developers about the implications of sharing Postman environments publicly.

The Postman data leak wasn’t a result of a flaw in the tool itself but rather how it was used. While powerful, the platform’s features for sharing and collaboration require careful implementation and adherence to security best practices.
This incident underscores the need for technical rigor, including enforcing strict access controls, educating developers, and adopting automated tools to identify and mitigate misconfigurations before they result in exposure. It also underscores the growing threat of API abuse, where vulnerabilities and misconfigurations can be exploited to steal data, disrupt services, and compromise systems.
To effectively reduce the risks associated with API development and management, and to ensure robust security across all stages of the software lifecycle, organizations need to adopt these best practices:
By implementing these steps, organizations can effectively reduce the likelihood of data leaks and enhance their overall API security posture.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
While implementing best practices is essential for robust API security, implementing an API intelligence platform like Treblle enhances security, observability, and compliance. Here's how Treblle stands out:
Treblle actively monitors your APIs for unauthorized activities and potential threats. It automatically identifies and flags:
Treblle also ensures that teams are alerted instantly over slack and email, allowing them to respond quickly and prevent further damage.
Treblle provides complete visibility into API performance, usage, security, and governance, offering teams the data they need to manage APIs effectively. With Treblle, teams gain access to:
Treblle ensures your team has all the data they need to build and maintain enterprise-grade APIs.
One of Treblle’s standout features is its ability to assist organizations in maintaining compliance with data protection and privacy regulations.
Treblle automatically:
This comprehensive compliance support not only helps organizations meet regulatory requirements but also builds trust with stakeholders by safeguarding sensitive information.
The Postman data leak underscores the critical need for secure API practices. Misconfigured permissions, poor secrets management, and insufficient training contributed to exposing sensitive credentials, highlighting vulnerabilities in how APIs are managed—challenges we also uncovered in our comprehensive API report for 2024.
In response, Postman assured its users: "Postman is committed to ensuring the security of its users. We have introduced secret-protection policies to prevent public workspaces from exposing sensitive information and are continuing to enhance our security features to safeguard our community."
While this is a step in the right direction, organizations must adopt a dual approach: implementing best practices and leveraging API intelligence platform like Treblle. With real-time threat detection, compliance support, and enhanced observability, Treblle helps teams address vulnerabilities before they become incidents.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.