API Governance | Updated on: Jan 7, 2026 | 23 min read | By Phil Sturgeon | Reviewed by Savan Kharod

Phil Sturgeon is an API specialist, author, and open-source contributor with decades of experience in API design, governance, and distributed systems. A former core PHP contributor and board member of the PHP-FIG, he has led API initiatives at companies like WeWork and Stoplight. Phil is also the founder of Protect Earth, a UK-based reforestation charity, and continues to share his expertise through the *APIs You Won’t Hate* community, books, and consulting work.
Once you have multiple teams shipping services, “just build an endpoint” quickly turns into a mess of inconsistent naming, drifting contracts, undocumented behavior, and security gaps that only show up in production. And that’s exactly what API governance best practices are meant to prevent.
API Governance is about establishing clear standards, policies, and practices that guide how your organization designs, builds, deploys, and uses APIs. So they remain discoverable, secure, scalable, and reusable as your API surface grows.
In this article, we will talk about API Governance, help you understand the fundamental difference between API Governance, API management, and API security, and explain 12 API Governance best practices that every API-first team follows.
By the end, you’ll have:
A best-practices checklist you can implement immediately
A lightweight operating model (who owns what)
A 30/60/90-day rollout plan for standards, automation, and runtime governance
API governance is the set of standards, policies, and practices that guide how an organization designs, develops, deploys, and uses APIs, ensuring its API portfolio remains discoverable, secure, scalable, and reusable as it grows.
At a practical level, governance exists to prevent “API drift” once multiple teams are shipping: inconsistent data shapes, inconsistent error handling, and multiple authentication patterns that pile up into real integration and security costs.
The API lifecycle is the concept of an API being planned, born, evolving over time based on usage and feedback, and eventually deprecated and sunset, possibly replaced by a new API that is starting its own lifecycle. This is the best write-up I've seen on the topic: Full API lifecycle management: A primer.
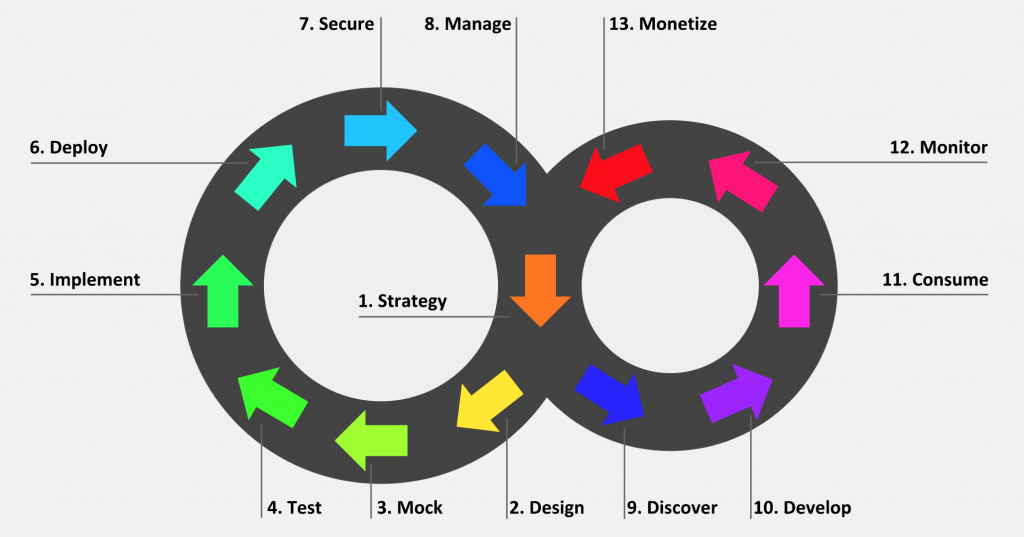
Diagram by Nicolas Massé, 2019, Solutions Architect at Redhat.
Every phase will be handled differently across organizations; some may be skipped, and that may be fine or a problem. Over time, different people will be involved for different overlapping bits. All of these phases have their own workflows and tooling to power them.
API Governance best practices are the repeatable standards and enforcement patterns that keep an organization’s APIs consistent, secure, and predictable as more teams ship more endpoints.
In practice, “best practices” exist because API programs drift. Organizations with multiple API teams will have noticed that their APIs start developing differences, different data formats, different error formats, multiple authentication systems, etc.
Over time, those differences compound into real cost: integrations become custom work, reuse drops, and older auth patterns can create security gaps.
So when people search for API governance best practices, they are not looking for a theoretical definition; they’re looking for a practical system that answers:
What do we standardize across APIs? (design conventions, error models, auth patterns, versioning rules)
How do we enforce it without slowing delivery? (contract-first workflows, linting, CI checks)
Who owns it? (platform team / API CoE / enabling team model)
How do we keep it working over time? (monitoring, feedback loops, deprecation discipline)
A simple way to frame it is that “API governance is about applying policy, process, and tooling across the entire API lifecycle, not a one-time checklist. That lifecycle includes planning, building, evolving based on usage and feedback, and eventually sunsetting APIs.”
API programs don’t fail because teams forgot governance. They fail because governance stays stuck as a document, while the API surface keeps growing. API Governance Best Practices for 2026 are therefore less about theory and more about repeatable, automatable guardrails: discover everything you run, standardize how APIs behave, enforce rules in CI, and continuously validate in production.
Here are the 12 API Governance best practices every API-first team should follow to help them implement governance like a system:
The first step in API governance best practices is building a single API catalog/registry that answers three questions for every API: what it is, who owns it, and where it is in its lifecycle (draft, active, deprecated, retired). A proper catalog is a centralized inventory that includes API metadata and ownership, so teams can discover and govern APIs consistently.
Without an inventory, governance becomes guesswork: duplicate APIs get built, standards drift across teams, and deprecated endpoints quietly stay in use. Most governance guidance starts with a comprehensive inventory and an up-to-date catalog, ideally kept up to date through discovery.
How to implement it:
Manual approach: Create a catalog entry for each API and require minimum fields: owner/team, contact, data classification, environments, version, and lifecycle status (active/deprecated/etc). Ownership + lifecycle metadata are repeatedly called out as “must-have” fields for discoverability and reuse.
Automated approach: Use a tool that discovers APIs and keeps the catalog up to date. Treblle, for example, provides an API Catalog for discoverability and supports controlled publishing based on ownership (only the API owner can publish), helping you maintain clean metadata and lifecycle visibility as part of governance.
A core part of API Governance Best Practices is making the API contract the thing everyone trusts, not “whatever production returns today.” The most practical way to do that is OpenAPI-first, because the OpenAPI Specification is a standard, language-agnostic interface description for HTTP APIs that tools (and humans) can understand without reading source code or inspecting traffic.
Once the OpenAPI contract is the source of truth, it becomes the backbone for consistent execution: it can drive reference documentation, enable mock servers for early consumer feedback, and power automated validation/contract testing. It can also flow into gateway operations; many gateways support importing OpenAPI definitions and validating requests against defined models/schemas, which turns “standards” into enforceable runtime behavior.
In practice, keep the OpenAPI spec versioned in source control and require spec updates via PRs for any behavior change. If you want to operationalize this faster, Treblle can auto-generate real-time API documentation, including endpoints and specs, and it can even use your OpenAPI spec as input for governance scoring and insights, keeping the contract central across docs and governance workflows.
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
Even if you’re OpenAPI-first, your API program can fall apart when every team makes reasonable but different design choices, different resource naming, different error payloads, and different pagination patterns. That’s why mature programs publish a single API style guide so APIs feel like they were designed by one team, not ten.
Keep the guide opinionated on the things that cause the most drift: resource and field naming, a consistent error model, pagination rules, and standard conventions like filtering/sorting and idempotency.
The key is making the guide enforceable. Instead of relying on manual review, use OpenAPI linting with a ruleset engine like Spectral to automatically validate specs against your style guide in PRs/CI.
If you’re using Treblle, you can reinforce this with shift-left governance via API design guidelines and portfolio-level quality scoring, so you can spot design inconsistencies early and track improvement over time.
One of the fastest ways to operationalize API governance best practices is to stop treating governance as a meeting and start treating it as policy-as-code. When governance rules run automatically in CI/CD, teams get immediate feedback on every change, and your standards stay consistent even as the API surface and the number of contributors grow.
In practice, this starts with OpenAPI linting. Tools like Spectral are built to apply rulesets to OpenAPI and other JSON/YAML specs, so you can encode your style guide and governance requirements into a ruleset and run it as a PR/CI status check.
This is what makes governance enforceable: missing security requirements, inconsistent naming, undocumented responses, or non-standard error models are caught before merge, not after consumers start integrating.
The second piece is breaking-change detection. Even well-designed APIs drift when changes aren’t compared against what already exists. Add an OpenAPI diff step that compares the “current” spec with the “proposed” spec, blocks merges if it detects breaking changes, and generates a human-readable changelog for reviewers. Tools like oasdiff are explicitly designed to identify breaking changes and produce change reports from OpenAPI diffs.
If you’re using Treblle, you can complement CI enforcement with an ongoing governance layer that scores APIs across design, security, and performance so you can spot regressions and track improvements across the whole API ecosystem, not just per-PR.
One of the highest-leverage API governance best practices in 2026 is shifting governance before code ships. Instead of discovering inconsistencies after an endpoint is live, you review the API contract early, align on naming/errors/pagination up front, and validate that the design actually supports the consumer workflow.
Mocking is what makes this practical. Generating a mock server from an OpenAPI design lets teams prototype the API without writing backend code, shorten the feedback loop, and avoid late rewrites that happen when feedback arrives after implementation.
To operationalize this, make “design review and mock” a standard step for new endpoints and breaking changes: OpenAPI PR first, mock server available for stakeholders, then implementation.
If you want to reinforce this with governance tooling, Treblle positions governance as shift-left rule enforcement, with API design guidelines and best-practice checks so teams can catch issues early and keep standards consistent as the API surface grows.
Contract testing is where API governance best practices stop being “guidelines” and become an automated safety net. The idea is simple: if your OpenAPI definition is the contract, then your build pipeline should continuously prove that the implementation still conforms to that contract: status codes, schemas, headers, and edge cases included.
In practice, you make this a standard CI step by running contract tests generated from the OpenAPI spec, so coverage grows automatically as your spec grows. Tools like Dredd are explicitly built to validate an API description document against the backend implementation, and tools like Aspen (with Alfred AI integration) can generates tests directly from your OpenAPI schema, including high-variation inputs that catch corner cases.
If you want enforcement beyond CI, request/response validation middleware can validate traffic against the spec at runtime.
If there’s one area where API governance cannot be “best effort,” it’s security. The OWASP API Security Top 10 exists for a reason: the same classes of failures keep showing up, especially around authorization and authentication, and governance is how you prevent those mistakes from repeating across every team and every endpoint.
A practical baseline for 2026 is straightforward: TLS everywhere, consistent AuthN/AuthZ, sensible rate limiting, and a standard set of HTTP security headers. NIST publishes concrete guidance on selecting and configuring TLS implementations, and OWASP maintains dedicated guidance on security headers and recommended configurations. Both are useful reference points when you formalize what “secure by default” means in your org.
Remember, the key here is enforcement. Treat these requirements as policy, validate them in CI, and keep validating at runtime. This is also where Treblle can fit naturally into the governance workflow.
Treblle’s API Governance capability includes API security scoring and runtime security risk assessment, and its API Security product describes automated checks on every API request, including things like authorization headers and SSL, while API Compliance can help flag regulated or sensitive data in requests/responses for standards like GDPR/CCPA/PCI.
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
A solid deprecation policy is one of those API governance best practices that pays for itself the first time you need to change a widely used endpoint. The goal is predictable change: clear rules for backward compatibility, a published timeline, and a consistent “sunset” process so consumers are never surprised. Swagger’s guidance is explicit here: you need a defined sunset period after you announce deprecation so API consumers have time to migrate.
In 2026, the most practical approach is to make the deprecation contract visible and process-driven. Mark deprecated parameters directly in your OpenAPI contract (for example, deprecated: true), and pair it with a timeline and migration guidance.
For timelines, you do not need to copy a giant company’s policy, but it helps to anchor your own. Microsoft Graph, for example, states that it deprecates versions/APIs at least 24 months before retirement, while other platforms commonly document shorter deprecation periods; for instance, Google Maps notes that its deprecation periods are around 12 months.
Operationally, this becomes sunset mechanics: announce early, publish a changelog, ship a migration guide, and track usage of deprecated endpoints until it drops to zero, and then retire.
Tools like Treblle can support this governance loop by combining a catalog and an ownership layer with runtime visibility, so you can see who is still calling deprecated endpoints, measure impact, and manage rollouts with fewer surprises.
Good docs are not nice-to-haves; they are a governance control. When API documentation is incomplete or inconsistent, consumers rediscover the same edge cases, integrations take longer, and support becomes the default onboarding path.
That’s why practical API governance best practices treat documentation as a required deliverable: clear usage guides, code samples, SDKs, and troubleshooting guidance, all easy to find and kept up to date.
The DX bar in 2026 is simple: developers should be able to go from zero to their first successful call with minimal back-and-forth. That usually means pairing reference docs (endpoints, params, responses) with task-based guides (common workflows) and copy-pasteable examples.
You can see this pattern in many mature API documentation examples, such as Stripe’s quickstarts and tour content, and in platform references, such as Azure’s REST API docs that walk developers through making real calls.
To keep documentation governed and not manually maintained, use tools like Treblle that can auto-generate real-time API documentation (endpoints, authentication, OpenAPI specs) and support API Catalog publishing for discoverability, keeping docs aligned with what’s actually running.
Stop writing docs manually—generate and update them automatically.
Treblle builds clean, accurate API docs with zero extra effort.
Explore Treblle
Stop writing docs manually—generate and update them automatically.
Treblle builds clean, accurate API docs with zero extra effort.
Explore Treblle
Runtime governance is the part of API governance best practices that happens after release. You watch how APIs behave in production, then use that data to tighten standards and prevent repeat incidents.
At a minimum, you should continuously track latency, error rates, and availability, set clear reliability targets (SLAs/SLOs), and alert when an API drifts outside those targets. A common operational pattern is to tie SLOs to an error budget, so reliability directly influences how aggressively you ship changes.
This is not just about performance. OWASP calls out that APIs are vulnerable when logs are missing, lack detail, or are not continuously monitored, which is why logging and monitoring need to be part of your baseline, not an afterthought.
Treblle supports runtime governance by providing an API score across performance, quality, and security, along with the underlying insights, so teams can see exactly what is failing standards and what to fix first. It also includes runtime security risk assessment and governance insights, helping you maintain consistent reliability and security expectationsacross the entire API estate.

Change management enables sustainable versioning and deprecation. As part of your API governance best practices, every breaking or behavior-changing release should ship with three things: a clear changelog entry, direct consumer notifications, and a migration guide that tells people exactly what to do (and by when).
Mature platforms also set an explicit minimum notice window. Microsoft Graph, for example, declares versions and even individual GA APIs deprecated at least 24 months before retirement or removal.
Make deprecation visible where developers actually look. Mark deprecated operations in your OpenAPI contract and docs, and uses standard HTTP signals so clients get an in-band warning. RFC 8594 defines the Sunset response header to indicate when a URI is expected to become unresponsive, and the HTTP Deprecation header draft describes how to signal that a resource is deprecated and link to more context, including a replacement or migration path.
If you want to operationalize this, Treblle can help by centralizing documentation through API Catalog so the latest docs, SDK links, and migration notes live in one place, while keeping ownership clear since only the API owner can publish updates.
On the governance side, Treblle scores APIs and surfaces underlying issues across design, performance, and security, including checks like versioning and rate limiting, which is useful during rollouts because you can spot regressions while managing the change.
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
The fastest way to improve governance is to make it measurable. A good governance model should enable KPI tracking, especially when it is aligned to an API catalog and the API lifecycle, so you can report progress and prove impact over time.
A practical KPI set for API governance best practices in 2026 usually falls into five buckets:
Coverage: percentage of APIs in your catalog, with a clear owner, and with lifecycle status. This tells you whether governance even has the surface area under control.
Conformance: how many APIs pass your rules (lint pass rate, policy violations per release, baseline security requirements met). This is the “are we following our standards” metric.
Change safety: breaking changes caught before merge, and adherence to deprecation timelines. This shows whether governance is preventing consumer disruption.
Operational health: SLO compliance and incident rate. Google’s SRE guidance highlights latency and error rate as common SLIs that map cleanly to API reliability targets.
Developer experience: time to first successful call (often tracked as “time to first call”), plus onboarding friction like support tickets during integration. Many API-first teams focus on improving time-to-first-call as a leading DX metric.
If you are using Treblle, you can layer these KPIs with a portfolio view by tracking an API governance score per API, backed by detailed scoring across AI readiness, design, performance, and security. That makes it easier to benchmark where you are today, prioritize what to fix first, and show improvement release over release using consistent scoring criteria.
The API lifecycle never really “finishes”. It loops through constant feedback, and design decisions get revisited every time you add an endpoint, evolve a schema, or cut a new version. That is why there is no perfect time to start governance, but there is a clear advantage to starting now.
The fastest path is to start small, prove value, then scale. This only works if leadership is bought in and governance is positioned as a workflow improvement, not extra busywork. A small proof-of-concept helps teams feel the benefits early.
Start with visibility and the smallest set of standards that remove friction immediately.
Build a catalog that answers three questions for every API: what it is, who owns it, and its lifecycle status (active, deprecated, retired).
Make OpenAPI the baseline contract for any API you plan to touch. It becomes the shared language across teams and tools.
Define a minimal, non-negotiable rule set: naming basics, a consistent error format, auth requirements, and a versioning convention.
Pick 1–2 “high-traffic or high-pain” APIs and deliver quick wins: clean up the contract, tighten documentation, and remove obvious inconsistencies so teams feel the impact early.
If you want to accelerate this phase, tools like Treblle can help you centralize governance visibility and prioritize fixes by scoring APIs across design, performance, and security, with the underlying details behind the score.
Now you make governance repeatable by putting enforcement into your delivery workflow.
Convert your style guide into lint rules and run them on every PR. Linting early and often is cheaper than fixing problems after clients integrate.
Add a lightweight design review flow: new endpoints and breaking changes start as an OpenAPI change, reviewed before implementation.
Introduce mocks for any new surface area to enable consumers and stakeholders to validate workflows early and reduce late rework.
Add breaking-change detection on OpenAPI diffs and require explicit approval and comms artifacts when changes are incompatible.
This is also a good time to formalize “ownership in the loop” so the right team reviews changes, owns the contract, and owns the consumer communication.
In the final phase, governance becomes a production discipline with reliability targets and measurable progress.
Define API tiers (internal, partner, and public) and set expectations for each tier. Establish SLAs like uptime targets, acceptable response times, and alerts when an API falls outside those targets.
Tie SLOs to an error budget policy so reliability influences shipping decisions when the budget is burned.
Close the loop: use real production telemetry such as slow endpoints, recurring errors, and consumer friction to drive changes to standards, documentation, and the next set of backward-compatible improvements.
Publish a monthly maturity report: That has coverage (catalog and owners), conformance (lint and policy pass rate), change safety (breaking changes caught), and operational health (incident rate, SLO compliance).
At this point, Treblle can act as a runtime governance layer by continuously scoring APIs and surfacing detailed findings on design, performance, and security issues, so you can track maturity improvements across the entire API estate over time.
This is when governance becomes a slow, manual sign-off process that teams try to bypass. API governance often gets a reputation for heavy-handed processes that slow delivery, but it doesn't have to be that way if you treat it as guardrails, not gates.
Avoid it by keeping human review focused on what humans are best at: API shape, consumer impact, major breaking changes, and pushing everything else into automated checks.
A style guide that is not enforced becomes a PDF nobody reads. Modern governance works when the rules are applied locally and in CI using linting and policy-as-code, so standards are consistent and repeatable.
Avoid it by turning your standards into an OpenAPI ruleset (Spectral or similar) and running it as a required PR check.
If an API has no clear owner, governance, or incident response, both break down. Catalog guidance repeatedly highlights owner and status as critical fields for accountability and for knowing which APIs are safe to build on.
Avoid it by making “owner” and “lifecycle status” mandatory catalog fields, and by enforcing that only the owning team can publish or update catalog entries. Treblle, for instance, supports owner-controlled publishing for its API Catalog.
If governance lacks a safe escape hatch, teams will work around it. Good governance behaves like a paved path: it makes the compliant choice the easiest choice, while still allowing exceptions with visibility and accountability.
Avoid it by defining an exception workflow with three basics: the reason, the risk accepted, and an expiry date. Then make exceptions auditable and reviewable.
Design-time checks are not enough. Governance needs feedback from production, because standards should evolve based on real-world performance, usage, and security signals. OWASP also explicitly calls out that APIs are vulnerable when logs and infrastructure are not continuously monitored.
Avoid it by setting SLOs for key APIs, monitoring latency and error rates, and feeding recurring failures back into your rulesets and design standards. Tools like Treblle can support this by scoring APIs across design, performance, and security and showing the underlying findings so teams know exactly what to fix first.
The real value of API Governance best practices is not the document you publish. It is the consistency you can enforce every time an API changes. In 2026, the teams that move fastest are the ones that treat governance as a system: know which APIs exist and who owns them, make the OpenAPI contract the source of truth, and automate standards so they are applied to every pull request, not just remembered in a meeting.
The OpenAPI Specification is built for exactly this kind of contract-driven workflow, since it provides a language-agnostic way to describe HTTP APIs that tools can validate and act on.
Governance also needs a hard security floor. OWASP’s API Security Top 10 keeps highlighting the same categories, including broken authorization and broken authentication, which is why baseline controls such as consistent AuthN and AuthZ, TLS, and abuse protection should be enforced by policy and continuously checked.
And once you ship, governance must continue at runtime. Reliability targets such as SLOs and an error budget policy help you turn production telemetry into clear decisions about when to ship changes and when to prioritize stability.
If you want to operationalize this without building a patchwork of scripts and dashboards, Treblle is designed to support governance both shift-left and in production by scoring APIs across design, performance, and security, along with run-time security risk assessments and the underlying details, so teams know what to fix first.
 API Governance
API GovernanceThis guide walks through 10 concrete Enterprise API Governance strategies to build an API governance framework that focuses on automation over manual gatekeeping, using contracts, policy-as-code, and AI-driven insights
 API Governance
API GovernanceManaging APIs at scale is harder than ever. Manual governance can’t keep up with growing complexity, compliance demands, and security risks. In this article, we explore how AI can transform API governance—making it smarter, faster, and fit for modern teams.
 API Governance
API GovernanceAPIs are the backbone of modern systems—but without governance, they can become your biggest liability. In this guide, we break down how engineering and product teams can avoid costly breaches by building API governance into every stage of the lifecycle.