API Security | Jul 1, 2025 | 8 min read | By Savan Kharod | Reviewed by Vedran Cindrić

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
As engineering teams scale, it’s common for new API endpoints to appear, some officially tracked, others hidden or unmaintained. This proliferation, known as API sprawl, introduces two critical blind spots: shadow APIs and zombie APIs.
In this article, I will define each, highlight the key differences between Shadow API vs Zombie API, and explain why addressing both is essential for security, compliance, and operational integrity.
A Shadow API refers to an API that operates outside the purview of an organization's IT and security teams. These APIs are often created without formal approval and lack proper documentation, making them invisible to standard monitoring tools. Common examples include:
Development or testing endpoints that were inadvertently exposed to the public.
APIs integrated by individual teams without centralized oversight.
Legacy APIs that remain active but are no longer maintained.
In September 2022, telecom major Optus' data breach exposed nearly 10 million customer records, not due to a public vulnerability, but because of an undocumented, unauthenticated API endpoint that wasn't on security’s radar. This shadow API lacked rate limits, authentication, or monitoring, providing easy access for anyone who discovered it.
A zombie API is a deprecated or abandoned endpoint that remains operational in your production environment, unused and unmaintained, but still functioning. Common examples of Zombie APIs include:
Temporary test or staging APIs, often created for troubleshooting or experimentation, are accidentally deployed to production and remain active long after their original purpose is served.
The old endpoints that aren’t turned off after upgrading to a newer API version (e.g., SOAP → REST)
In 2023, a deprecated SOAP-based patient data API in St. Luke’s Health System exposed 450,000 records because it was never fully decommissioned, even after the organization moved to REST services; the endpoint remained live, unpatched, and undetected for months.
Here are the key differences between Shadow APIs vs Zombie APIs:
| Aspect | Shadow API | Zombie API |
|---|---|---|
| Lifecycle Stage | Active and in use, but bypassed official processes. | Deprecated or no longer actively used, yet still operational. |
| Origin | Created for rapid prototyping, hacks, or quick fixes outside governance. | Result of incomplete deprecation, migration artifacts, or abandoned test APIs. |
| Visibility | Hidden, unknown to API gateway, logging, or security teams | Known but ignored, registered at some point, but no longer tracked |
| Documentation | Undocumented, not in OpenAPI/Swagger specs | Either removed from specs or listed, but without relevant documentation |
| Security Posture | Bypasses auth, rate limits, logging; high exploitation risk | No longer patched; may contain outdated SSL, old auth, or known CVEs |
| Governance Status | Never submitted to security review or API catalog | Once governed, but never formally retired |
| Operational Impact | Provides functionality outside expected channels; often unstable | Idle, carries maintenance debt, and adds noise to monitoring |
| Detection Difficulty | High, no logging or spec coverage; discovered via traffic inspection | Moderate, no traffic, but still visible in infrastructure; identified via spec diff. |
| Typical Risks | Undetected data leaks, unauthorized access points | Exploitation of old, insecure functionality causes breaches |
| Typical Remediation | Register, apply security controls, route through the gateway, or remove it. | Sunset cleanly, revoke access, update specs, and decommission the endpoint. |
Understanding shadow APIs vs. zombie APIs isn’t about closing off hidden weak spots in your system. Here’s what makes both of them significant:
Shadow APIs are live endpoints you didn’t track; they skip security checks and monitoring, making them prime targets.
Zombie APIs are deprecated services that continue to run. They often use old libraries or insecure protocols and lack patches.
Neither shadow nor zombie APIs get routed through gateways or logging. That means data can flow out, unmonitored and unchecked, potentially violating GDPR, CCPA, HIPAA, etc.
Shadow APIs bypass the approval and documentation process. Zombie APIs may have been approved once, but are never properly retired. That leads to drift in your API catalog and audit failures.
These APIs often show up on the radar only after a breach or during a costly audit, by then, you’re in reactive mode. Early detection through spec comparison, traffic monitoring, or inventory scans is more efficient and cost-effective.
Modern observability tools continuously monitor live API traffic, comparing actual calls against documented specs or schemas. They signal undocumented or inactive endpoints, commonly known as shadow APIs (undocumented but active) and zombie APIs (obsolete but still exposed). This real-time visibility is critical for effective API governance and risk management.
Treblle is an API intelligence platform that helps you make sense of your observability data with its targeted capabilities to uncover and manage shadow and zombie APIs efficiently:
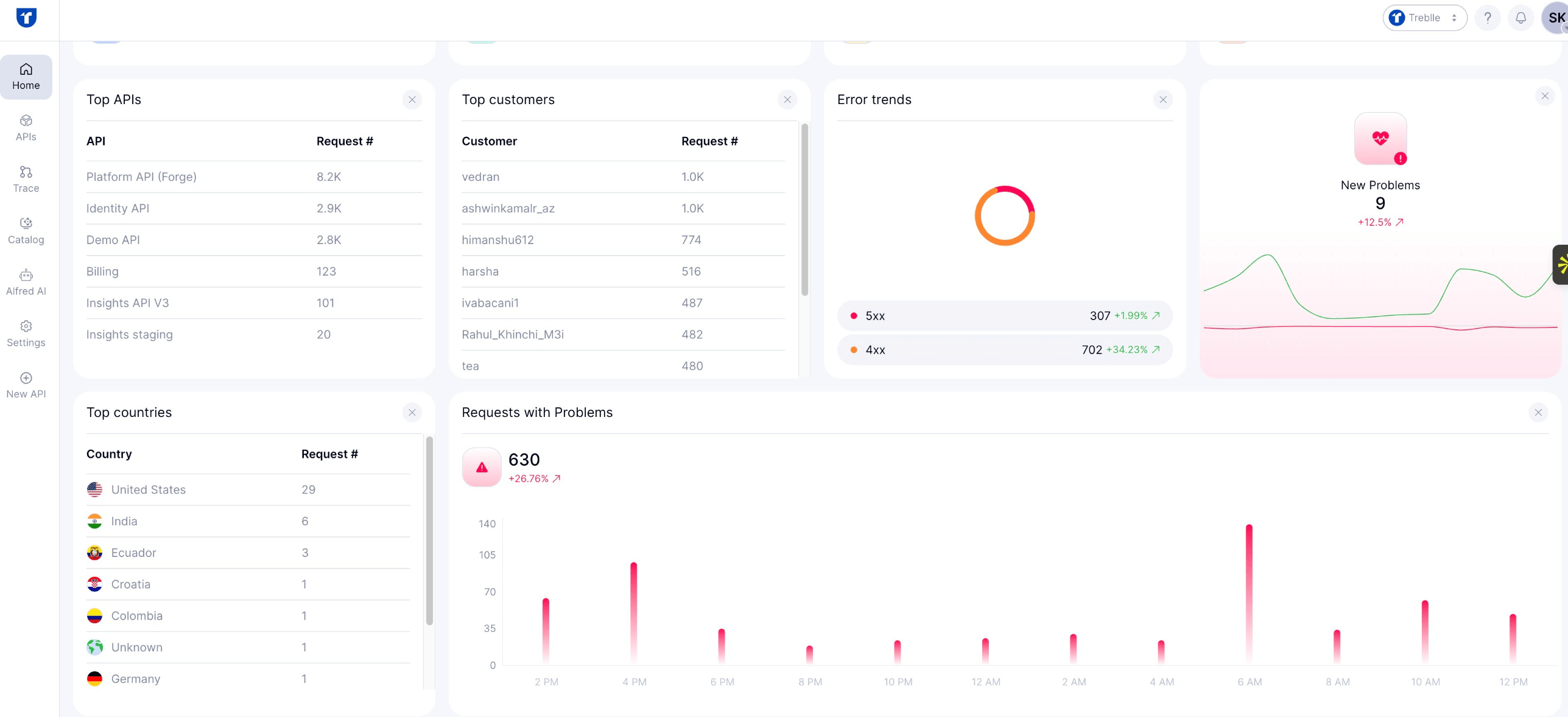
Dashboard
Treblle’s dashboard gives a centralized view of API activity, total requests, endpoint counts, compliance scores, recent request logs, performance trends, and threat levels, allowing you to identify unexpected endpoints.
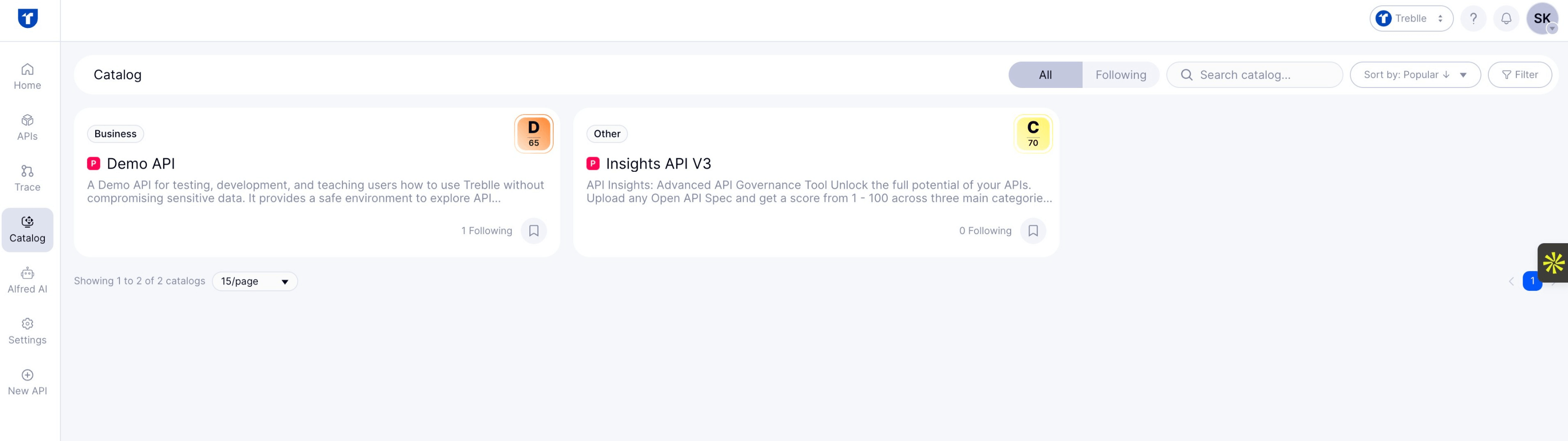
Automated Discoverability & Cataloging
Treblle’s API Catalog helps automatically discover and aggregate all active endpoints in one place. It enables teams to identify undocumented ("shadow") or unused ("zombie") APIs and categorize them by status or function.
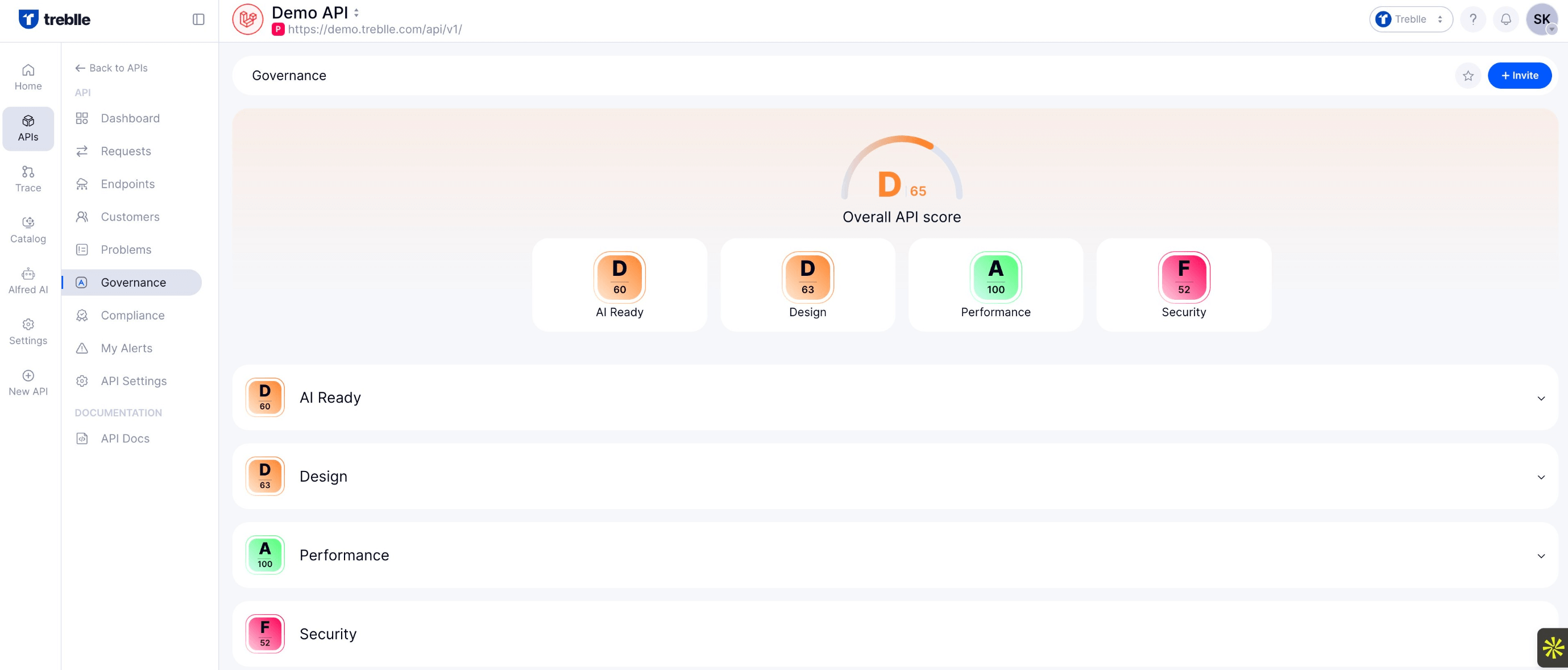
API Score
Each API is scored across AI readiness, performance, quality, security, and compliance. APIs that never register a score or suddenly drop out of the score panel signal potential shadow or zombie risk.
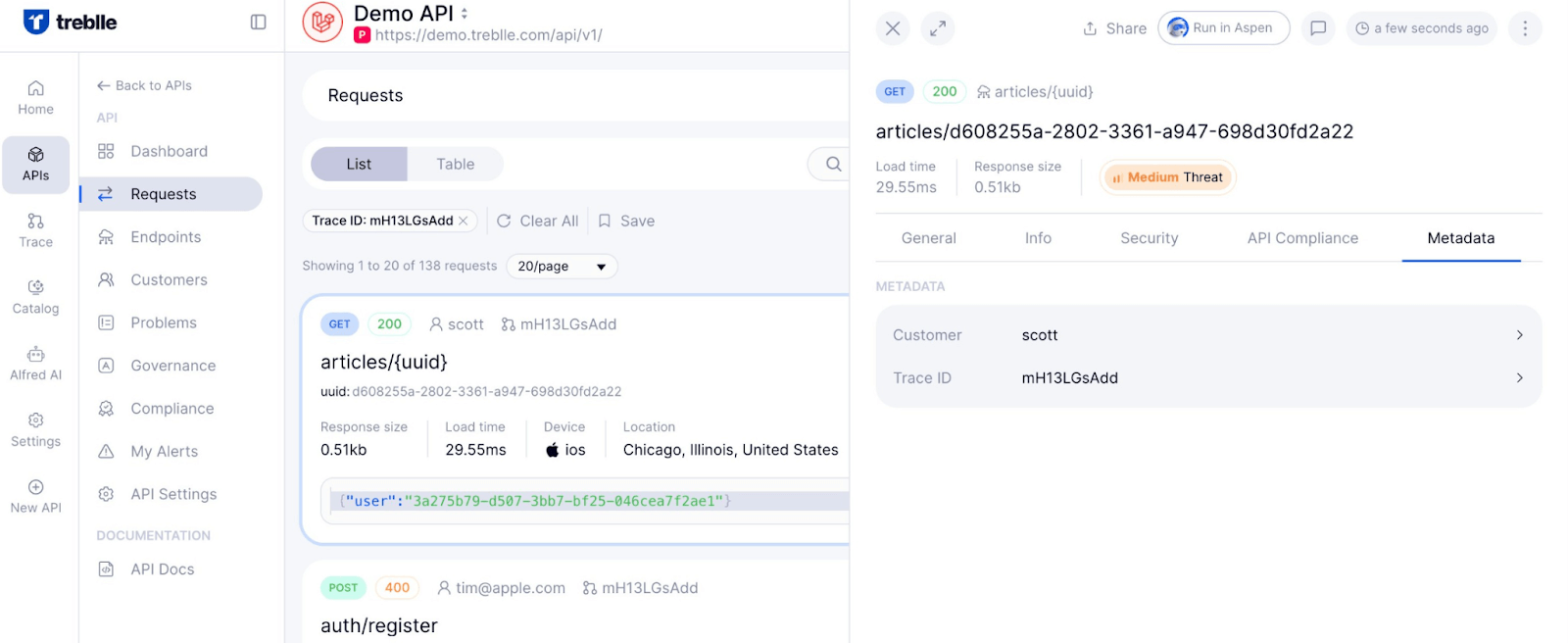
Traceability & Search Tools
With advanced trace IDs and real-time search filters, teams can trace request flows across microservices and filter by endpoint, client, or location, which is ideal for confirming suspected ghost APIs.
AI Assistant "Alfred"
Alfred is an intelligent assistant that helps teams discover and evaluate unknown endpoints. Alfred surfaces usage anomalies and flags endpoints with no historical documentation, reducing the time to detection.
Custom Alerts & Governance Checks
You can configure alerts for unexpected endpoint patterns, compliance deviations, or silent endpoints. Treblle also provides built‑in governance rules and automated compliance checks that help detect unused or risky APIs before they cause damage.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Prevent shadow endpoints with fully automated documentation as part of your CI/CD pipeline. By generating OpenAPI specs during builds and deployments, you ensure every new or changed API is captured and documented in real time, a proven way to eliminate undocumented APIs.
Define a clear API lifecycle, from design to decommission. This includes versioning, deprecation schedules, and retirement processes. Require business justification for every live endpoint, and verify its documentation and governance status before deployment.
Use tools or platforms to auto-discover every live endpoint across internal, external, and third-party environments. Monitor usage, documentation, versions, and ownership centrally. Regularly audit this inventory for undocumented (shadow) or unused/deprecated (zombie) APIs.
Analyze traffic patterns: endpoints with zero or extremely low usage over time may be zombie APIs. Shadow APIs often surface via anomalous traffic coming from unexpected clients or environments. Integrate this analysis into annual or quarterly security reviews.
Implement platforms that continuously scan your environment and compare runtime traffic against documented specs. Integrate these with governance dashboards, alerting, and compliance workflows to proactively flag new or inactive API endpoints.
All API requests should go through an API gateway, ensuring visibility, routing control, security scanning, and logging. Gateways help prevent shadow APIs by owning all external access and enforcing authentication and version policies.
Establish alerts for suspicious API behavior, such as unknown endpoints appearing, unused APIs lingering, or endpoints skipping governance. Couple this with automated lifecycle checks to detect and block endpoints that lack documentation or fail compliance criteria.
Educate developers, DevOps, and security teams about the dangers of shadow/zombie APIs. Encourage accountability, clearly assign API “ownership,” and make it part of dev workflows to document and retire endpoints systematically.
Shadow APIs are undocumented yet active endpoints that operate under the radar, while zombie APIs are outdated services that remain exposed and forgotten.
To avoid these hidden risks, you should embed automated documentation and discovery into your CI/CD pipeline, enforce lifecycle policies for deprecation and retirement, and maintain real‑time monitoring for unexpected or unused endpoints.
Treblle simplifies this process by automatically discovering all live APIs, scoring them on performance and security, and alerting you to undocumented or inactive services through its unified dashboard and discoverability features. Adopting these practices, supported by Treblle, ensures your API landscape remains clean, secure, and manageable now and is ready for future scale.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.