By industry
By initiatives
By industry
By initiatives
API Security | Jun 9, 2025 | 8 min read | By Savan Kharod

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
Shadow APIs have emerged as a significant security concern in today's API-driven development landscape. These undocumented and unmanaged APIs can introduce vulnerabilities, leading to data breaches and compliance issues.
This article delves into what Shadow APIs are, why they're dangerous, how they originate, and strategies for detection and prevention.
A Shadow API refers to an API that operates outside the purview of an organization's IT and security teams. These APIs are often created without formal approval and lack proper documentation, making them invisible to standard monitoring tools. Common examples include:
Unlike Zombie APIs, which are deprecated or obsolete yet still accessible, Shadow APIs are active but unmanaged, posing unique security challenges.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Shadow APIs often bypass established security protocols. Hence, they become easy targets for attackers without proper authentication, authorization, and encryption. For instance, a shadow API using outdated libraries like Log4j can expose organizations to known vulnerabilities such as Log4Shell, even if official systems are patched.
Shadow APIs operate outside standard monitoring tools and remain invisible to security teams. This lack of visibility means malicious activities, such as data exfiltration or unauthorized access, can go undetected for extended periods.
Unmonitored APIs can inadvertently expose sensitive data, leading to breaches of regulations like GDPR, HIPAA, or CCPA. For example, the Optus breach involved a shadow API that lacked proper access controls, resulting in unauthorized access to customer data. To better prepare your teams, read our guide for engineering and product teams on avoiding API breach pitfalls.
Each unmanaged API increases the organization's attack surface. Attackers can exploit these hidden endpoints to infiltrate systems, escalate privileges, or move laterally within networks.
Shadow APIs can lead to redundant functionalities, inconsistent data flows, and integration challenges. Over time, this results in increased maintenance costs and hampers system upgrades or migrations.
In the event of a security incident, undocumented APIs complicate forensic investigations. Without knowledge of all active endpoints, determining the breach's scope and implementing corrective measures becomes arduous.
In fast-paced development cycles, teams frequently create APIs for testing or staging purposes. These endpoints, intended for temporary use, sometimes inadvertently make their way into production environments without proper decommissioning, resulting in unmanaged shadow APIs. Following best practices for deprecating an API can help ensure these temporary endpoints are formally retired before becoming security risks.
Microservices architectures promote modular development, allowing teams to deploy services independently. However, without centralized oversight, some microservices may expose APIs that aren't registered or monitored, leading to the proliferation of shadow APIs within the system. This highlights the importance of applying API governance best practices to maintain oversight, even in decentralized architectures.
Integrating third-party services can introduce shadow APIs, especially when these integrations occur without thorough vetting or documentation. Such APIs might bypass standard security protocols, increasing the risk of vulnerabilities.
Older systems often contain APIs that were once active but have since fallen out of use. If not properly retired, these forgotten endpoints remain accessible and unmanaged, effectively becoming shadow APIs that can be exploited.
Employees or departments might deploy APIs without informing the IT or security teams, aiming to address immediate needs. Such unauthorized deployments, lacking formal approval and oversight, contribute to the shadow API landscape.
Recognizing these common sources of shadow APIs is the first step toward mitigating their risks.
Detecting Shadow APIs is crucial for maintaining a secure and compliant API ecosystem. These hidden endpoints can introduce vulnerabilities, leading to data breaches and compliance issues. Many of these detection challenges are part of broader issues teams face with API complexity. Learn how AI is helping solve these common API challenges across the lifecycle.
Below are strategies and tools to effectively detect Shadow APIs:
API discovery tools are essential for uncovering shadow APIs within your infrastructure. They automatically scan and catalog all API endpoints, providing visibility into undocumented or unauthorized APIs.
Treblle is an API intelligence tool that, once integrated, instantly maps your entire API landscape, generating real-time inventories and eliminating shadow APIs. Treblle tracks every API request and response, surfacing performance issues, anomalies, and SLA breaches across all services.
Advanced analytics provide insights into traffic, latency, endpoint usage, and client behavior, facilitating debugging, optimization, and scaling.
Other notable tools include:
Monitoring network traffic can reveal unexpected API calls, indicating the presence of shadow APIs. API gateways serve as centralized points to manage and monitor API traffic, ensuring all API calls are authenticated and authorized. Tools like Treblle, Kong, MuleSoft, and AWS API Gateway offer such capabilities.
Artificial Intelligence (AI) and Machine Learning (ML) can analyze API usage patterns to detect anomalies. Unusual behavior, such as spikes in traffic or access from unexpected sources, may indicate shadow API activity. Implementing AI-driven security solutions can enhance the detection of such anomalies. You can explore more in our article on the 8 benefits of using AI in your API workflows.
Preventing and eliminating Shadow APIs is essential for maintaining a secure and compliant API ecosystem. Below are strategies and best practices to mitigate the risks associated with shadow APIs:
Implement clear policies defining API development, deployment, and decommissioning processes. This includes aligning governance efforts with AI capabilities for improved visibility and compliance — as discussed in our guide on AI, API Governance & Compliance.
Ensure all APIs undergo proper documentation, approval, and security assessments before going live. Regularly review and update these policies to adapt to evolving security landscapes.
Create and regularly update an inventory of all APIs within the organization. This inventory should include details such as API endpoints, versions, owners, and their respective documentation. A well-maintained inventory aids in identifying unauthorized or outdated APIs that may pose security risks.
Incorporate security measures early in the API development process. Developers can identify and address potential vulnerabilities by embedding security checks into the CI/CD pipeline before deploying APIs. This proactive approach reduces the likelihood of shadow APIs emerging unnoticed.
Deploy API gateways to manage and monitor API traffic effectively. These gateways can enforce authentication, rate limiting, and logging, providing visibility into API usage patterns. Monitoring tools can detect anomalies and unauthorized access attempts, enabling prompt responses to potential threats.
Leverage tools like Treblle, which automatically discover and document APIs within your infrastructure. Treblle helps identify undocumented APIs, ensuring they’re brought under proper management and aligned with security protocols. Automated documentation also streamlines maintenance and simplifies auditing. You can explore some of the top API documentation tools to see how solutions like Treblle compare.
Schedule periodic security assessments to evaluate the integrity of your API ecosystem. Penetration testing can uncover hidden vulnerabilities, including those in shadow APIs, allowing for timely remediation. Regular audits ensure compliance with security standards and help maintain a robust security posture.
Educate developers and stakeholders about the risks associated with shadow APIs and the importance of adhering to security protocols. Encourage open communication regarding API development and usage to prevent unauthorized implementations. A security-conscious culture is vital for the early detection and prevention of shadow APIs.
Understanding the differences between Shadow APIs and Zombie APIs is crucial for maintaining a secure and compliant API ecosystem. Here’s the difference between the two:
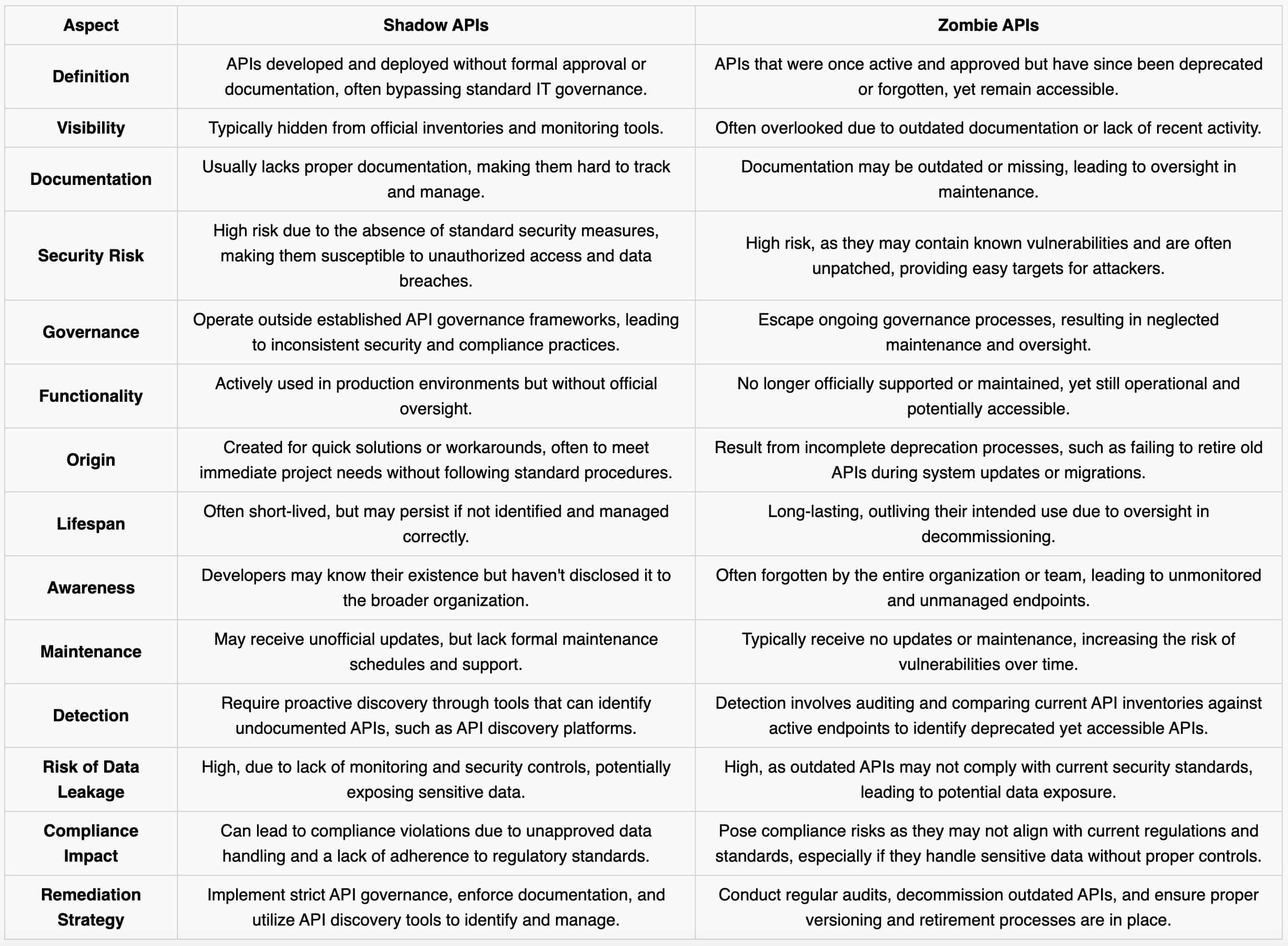
Shadow APIs, undocumented and unmanaged endpoints, pose significant security and compliance risks. Proactively identifying and managing these hidden APIs is crucial for maintaining a secure and efficient API ecosystem.
Treblle offers a comprehensive solution to this challenge. With real-time API monitoring, automated documentation, and insightful analytics, Treblle provides the visibility needed to effectively detect and eliminate shadow APIs.
Its user-friendly interface and seamless integration capabilities make it an invaluable tool for organizations aiming to enhance their API observability and governance.
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
Bring policy enforcement and control to every stage of your API lifecycle.
Treblle helps you govern and secure your APIs from development to production.
Explore Treblle
 API Security
API SecurityThree Chinese AI labs stole 16 million Claude interactions without triggering a single obvious alarm. They didn't hack anything. They just looked like regular users—until the numbers told a different story.
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.