Other | Nov 10, 2025 | 13 min read | By Savan Kharod

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
On June 3, 2025, ethical hackers Gal Nagli, Sam Curry, and Ian Carroll discovered a critical vulnerability in the FIA's Driver Categorisation portal that took them just 10 minutes.
Within that brief window, they gained complete access to Max Verstappen's passport, CV, FIA Super License, and password hash. But the exposure didn't stop with the three-time F1 World Champion. The breach compromised personally identifiable information (PII) for approximately 7,000 drivers across multiple motorsport categories, including Lando Norris, Fernando Alonso, and Nico Hülkenberg.
The hackers immediately reported their findings to the FIA. By June 10, the vulnerability was patched. The organization confirmed that no malicious actors had exploited the flaw, and driver data remained secure.
But here's the uncomfortable reality: if ethical hackers found this vulnerability in 10 minutes, how long would it have taken bad actors? And what would they have done with 7,000 driver records, passport scans, and password hashes?
This breach exposes a fundamental problem in modern API security: organizations that handle sensitive data often miss basic security vulnerabilities until it's too late. The FIA got lucky. Most organizations don't.
In this article, we will break down what caused the breach and how using tools like Treblle could have prevented this breach from happening in the first place.
The vulnerability exploited by the researchers is called mass assignment - a common API security flaw that occurs when applications blindly accept client-side input without server-side validation.
Here's how the attack unfolded:
The researchers signed up for a regular driver account on the FIA Driver Categorisation portal, the same system the FIA uses to manage driver classifications (Bronze, Silver, Gold, and Platinum ratings) that are crucial for endurance racing eligibility. This is a public-facing portal where drivers create accounts and upload documents like passports, driver's licenses, and race results for validation.
They completed the registration process like any normal user would. No special tools. No sophisticated techniques. Just a standard account creation.
While testing the portal's functionality, the researchers began examining the site's underlying code. By analyzing the JavaScript, they discovered something interesting: the portal's framework included multiple role types, drivers, FIA staff, and administrators.
More importantly, they noticed a "roles" parameter in the JSON response when updating their profile. The HTTP PUT request used to update user profiles was relatively simple and didn't contain many interesting attributes on the client side.
However, the JSON response from the server revealed additional values, including the roles parameter that wasn't being properly validated.
Based on what they found in the JavaScript, the researchers hypothesized that they could modify their account role by sending a crafted HTTP PUT request. They guessed the correct request format to update their roles parameter, changing it from "user" (or "driver") to "admin."
The request looked something like this:
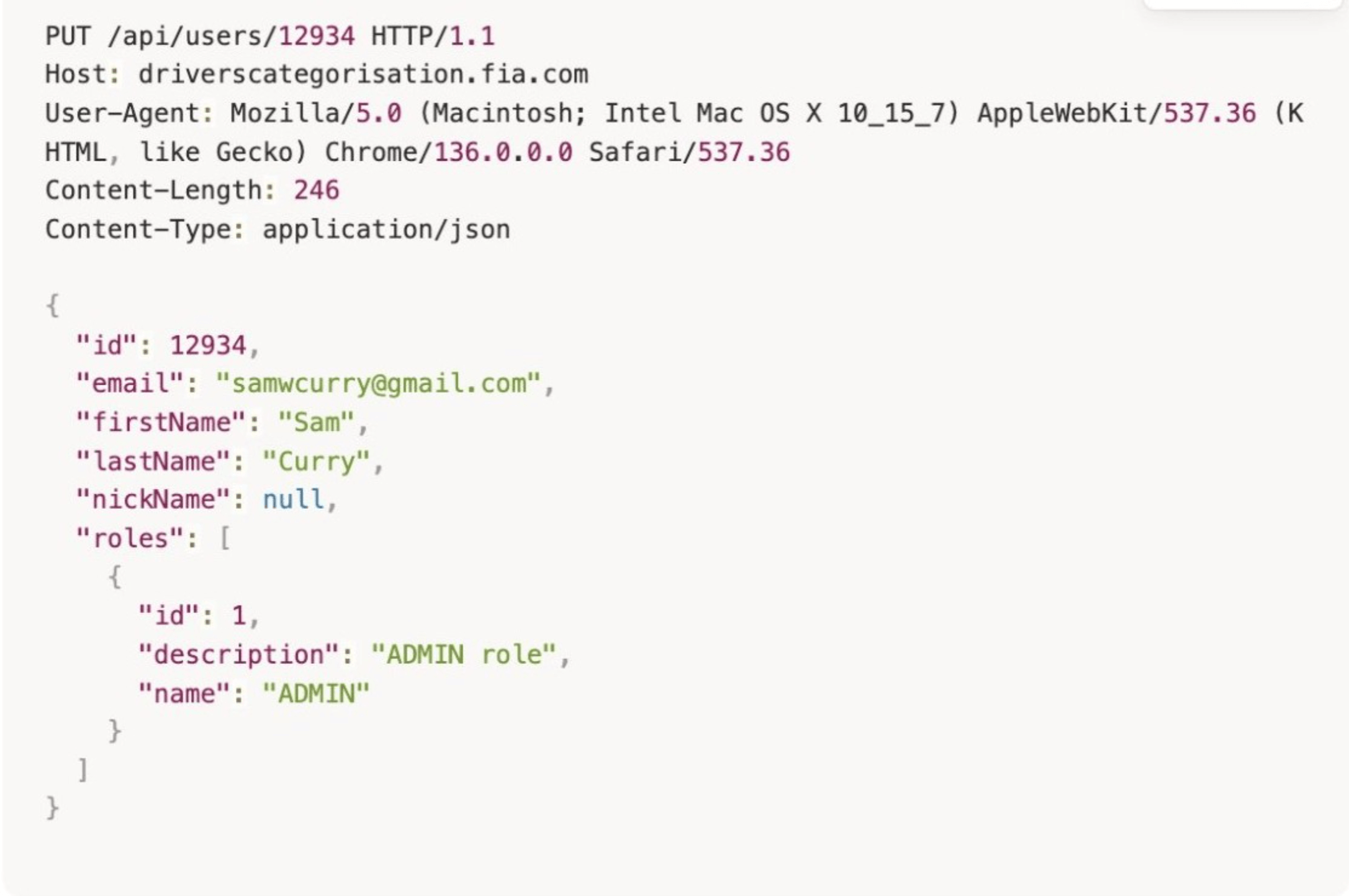
The critical flaw: the API accepted this client-side role modification without any server-side validation. There were no checks to verify whether the user making the request actually had permission to change their own role. The server simply trusted the input and updated the database accordingly.
When they submitted the modified HTTP PUT request, the server processed it without question. No authorization checks. No administrative approval workflow. No multi-factor authentication requirement. No audit logging that would trigger alerts.
The API's logic essentially said: "A user wants to update their profile? Sure, I'll accept whatever parameters they send me, including role changes."
This is called ‘mass assignment,’ when an application automatically binds client-provided data to internal objects or database models without filtering which fields should be modifiable by users.
Upon logging back into the portal, the researchers found themselves in a completely different interface, the FIA's internal dashboard for managing driver classifications across all motorsport categories.
The admin panel revealed:
Complete driver database access across all FIA-sanctioned series
Internal management tools for Bronze, Silver, Gold, and Platinum categorizations
Document review systems showing uploaded passports, licenses, and race results
Communication threads between FIA officials and drivers
Committee evaluation notes and performance assessments
To verify the breach was real and not just a front-end UI glitch, they, being F1 fans, tried to access Max Verstappen's profile, and as expected, they could access his passport, resume, FIA Super License, and password hash. They were also able to view the comments from FIA's internal committee members on the status of the drivers. After that, they immediately stopped testing.
The FIA breach wasn't the result of sophisticated hacking. It was the consequence of fundamental security failures that plague API development across industries.
The Driver Categorisation API accepted role changes from client-side requests without server-side verification. This violates a core security principle: never trust user input. Every parameter modification, especially those affecting permissions and access levels, must be validated on the server.
Zero-trust security assumes that no request, internal or external, should be trusted by default. The FIA's API operated on implicit trust: if a request came from an authenticated session, it was processed. This approach fails the moment an attacker gains initial access through legitimate credentials.
Admin privileges should be protected by multiple layers of validation. Changing a user's role from standard to admin should require:
Server-side permission checks
Administrative approval workflows
Audit logging of privilege escalation attempts
Multi-factor authentication for sensitive operations
None of these safeguards were in place.
Mass assignment vulnerabilities are well-documented in the OWASP API Security Top 10 (specifically under "Broken Object Level Authorization"). Security testing should have caught this flaw before production deployment. The fact that ethical hackers found it in 10 minutes suggests that comprehensive API security testing wasn't part of the development lifecycle.
Even if the vulnerability made it to production, runtime monitoring should have detected the privilege escalation attempt. When a newly created account immediately attempts to modify its role to admin, that's an anomaly that should trigger alerts.
The FIA had no visibility into this activity until ethical hackers reported it.
API security failures like the FIA breach aren't inevitable. They're preventable with the right tools, visibility, and Governance. Here's how Treblle's platform would have stopped this attack at multiple stages.
Treblle's API Intelligence provides complete visibility into every API call, including request parameters, response data, and user behavior patterns.
If the FIA had deployed Treblle on their environment, or specifically on the Driver Categorisation API, the platform would have:
Mapped every endpoint and parameter: Treblle automatically discovers all API endpoints and catalogs the data they handle. The role parameter would have been flagged as sensitive during initial mapping.
Detected unusual request patterns: When the researchers modified their HTTP PUT request to include a role change, Treblle would have captured this as an anomaly. A newly created account attempting to escalate privileges is a red flag that triggers immediate investigation.
Identify the origin of the breach: Treblle logs comprehensive details about every API call: user agent, IP address, geolocation, request timing, payload structure, and response codes. Security teams would have seen exactly when the privilege escalation occurred, from which IP address, and what data was accessed afterward.
Alerted teams within seconds: Instead of discovering the breach through external researchers, the FIA's security team would have received real-time alerts the moment suspicious activity began.
The breach window wouldn't have been 10 minutes. It would have been seconds.
Treblle's security layer continuously scans API traffic for vulnerabilities, suspicious patterns, and compliance violations.
In the FIA scenario, Treblle Security would have:
Identified the mass assignment vulnerability: Treblle analyzes request patterns to detect when APIs accept unvalidated input for sensitive parameters. The role modification attempt would have been flagged immediately as a potential mass assignment attack.
Detected PII exposure: The moment passport scans, license documents, and password hashes were accessed, Treblle would have generated high-severity alerts. The platform recognizes sensitive data types and flags any unusual access patterns.
Enforced GDPR compliance checks: Driver data falls under strict data protection regulations. Treblle automatically checks for GDPR compliance violations, including unauthorized access to personal data, lack of encryption, and insufficient access controls.
Generated security scores for every API call: Treblle assigns risk scores to API requests based on behavior, data sensitivity, and access patterns. A newly created account accessing thousands of passport scans would receive a maximum risk score, triggering immediate lockdown protocols.
Traditional security tools react after breaches occur. Treblle detects threats in real-time, before data leaves your infrastructure.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
The best way to prevent breaches is to catch vulnerabilities before they reach production. Treblle's Governance layer enforces security policies throughout the API lifecycle.
With Treblle Governance, the FIA could have:
Enforced schema validation: Governance policies would have required explicit server-side validation for any role or permission changes. The mass assignment flaw would have been caught during API design reviews, not after deployment.
Implemented least-privilege access controls: Treblle enforces policies that ensure users can only access data and perform actions appropriate to their role. Attempting to escalate privileges without proper authorization would be blocked at the API gateway level.
Required contract testing for sensitive endpoints: Any endpoint handling authentication, authorization, or PII would be subject to strict contract testing. Changes to role parameters would require explicit approval and validation logic.
Blocked unauthorized privilege escalations at runtime: Even if the vulnerability made it to production, Treblle's runtime Governance would have intercepted the malicious request and alerted the right team to block it.
Governance isn't just about compliance. It's about building security into your APIs from the ground up, so vulnerabilities like mass assignment never reach production.
Speed matters in security. The difference between a contained incident and a catastrophic breach often comes down to response time.
Treblle's custom alerting system would have:
Triggered immediate notifications: The moment the first privilege escalation attempt occurred, Treblle would have sent alerts via Slack, email, or webhook to the FIA's security team.
Flagged sensitive data access: When the researchers accessed passport scans and license documents, Treblle would have generated alerts specifically for PII exposure, ensuring the incident was escalated to the appropriate teams.
Detected anomalous access patterns: A single account accessing thousands of driver records in rapid succession is abnormal behavior. Treblle's anomaly detection would have identified this pattern and triggered alerts before significant data was compromised.
Instead of learning about the breach from ethical hackers, the FIA's security team would have been alerted within seconds of the first suspicious request. Response time would have shifted from days to minutes.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
The FIA breach isn't an isolated incident. It's part of a broader pattern of API security failures in organizations that handle sensitive data.
Sports organizations, regulatory bodies, and credentialing systems manage massive amounts of PII: athlete medical records, performance evaluations, licensing information, and personal identification documents.
These organizations are subject to strict data protection regulations like GDPR, yet many lack the API security infrastructure to protect the data they're entrusted with.
Consider the parallels:
Jaguar Land Rover's breach exposed similar vulnerabilities in authentication systems. Like the FIA, JLR's APIs lacked proper access controls and runtime monitoring.
Healthcare API breaches consistently exploit broken object-level authorization and mass assignment flaws, exposing patient records and medical histories.
Financial services APIs have suffered similar attacks where privilege escalation vulnerabilities allowed unauthorized access to account data.
The pattern is clear: organizations underestimate API security until it's too late. They invest in perimeter security, network monitoring, and endpoint protection, but neglect the APIs that actually handle their most sensitive data.
APIs are the backbone of modern digital infrastructure. They're also the most common attack vector. According to Gartner, APIs will be the most frequent attack vector by 2025, accounting for over 50% of security incidents.
The FIA breach proves this prediction is already a reality.
The FIA was fortunate. Ethical hackers discovered the vulnerability and reported it responsibly. But luck isn't a security strategy.
In the same 10-minute window that it took researchers to find and exploit the mass assignment flaw, malicious actors could have:
Exfiltrated 7,000+ driver records to sell on the dark web
Used password hashes for credential stuffing attacks across other platforms
Impersonated drivers using stolen passport data for identity fraud
Accessed internal FIA communications to gain competitive intelligence
Modified driver categorizations or licensing data to manipulate race eligibility
The consequences could have extended far beyond privacy violations. They could have compromised the integrity of motorsport itself.
Mass assignment vulnerabilities are common but preventable: They occur when developers prioritize speed over security, trusting client-side input without validation. Comprehensive security testing and Governance policies eliminate these flaws before deployment.
Real-time monitoring is essential for regulated industries: Organizations handling sensitive data can't afford blind spots. API Intelligence provides the visibility needed to detect threats in real-time, not days or weeks after the fact.
Zero-trust architecture requires server-side validation: Never trust user input. Every parameter modification, especially those affecting permissions, must be validated on the server with explicit authorization checks.
Governance at design time prevents breaches at runtime: Security can't be an afterthought. Building Governance into the API development lifecycle ensures vulnerabilities are caught before they reach production.
The FIA was lucky that ethical hackers found their vulnerability first. Most organizations aren't that lucky.
API security failures are preventable. Mass assignment vulnerabilities, privilege escalation flaws, and broken access controls can all be detected and mitigated before they're exploited, but only if you have visibility into what your APIs are actually doing.
Traditional security tools are reactive. They detect breaches after data has been compromised, then help with incident response and forensics. Treblle is proactive. The platform provides complete visibility into every request, response, and data flow across your API infrastructure.
Treblle monitors every API request in real-time, detects vulnerabilities such as mass assignment flaws, and alerts your team before data is exposed. Don't wait for ethical hackers to find your security gaps.
Treblle also automates vulnerability detection, runtime threat prevention, and Governance and compliance enforcement
Don't wait for ethical hackers to find your security gaps; let Treblle help.
 Other
OtherIn Sept 25, JLR suffered a major cyber attack. In this article, we provided a complete breakdown of the JLR breach, detailing what happened, how it occurred, and the lessons learned.
 Other
OtherThe newly developed Treblle Next.js SDK supports the App Router, Pages Router, and Edge runtime.
 Other
OtherOn June 26, 2025, we hosted a webinar with API security expert Colin Domoney and Treblle’s Vedran Cindrić to unpack what really breaks API security. Here are the key takeaways, including real breach examples, common myths, and a practical security checklist.