API Security | Jan 10, 2025 | 8 min read | By Savan Kharod | Reviewed by Vedran Cindrić

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
In late December 2024, Volkswagen Group, a global leader in the automotive industry, became the center of a shocking data breach that exposed the sensitive information of around 800,000 electric vehicle (EV) drivers. This breach, caused by a misconfigured API, highlights the pressing need for stronger API security practices in an era where APIs power almost every digital experience.
This article will examine the breach in more detail, including what caused it and what the company could have done better to prevent it.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Reports from Der Spiegel, The Verge, and Electrek reveal that the breach originated from a misconfigured Amazon Web Services (AWS) cloud storage managed by Cariad, Volkswagen’s software subsidiary. This vulnerability left an API exposed, allowing access to a trove of sensitive data for an extended period before it was discovered.
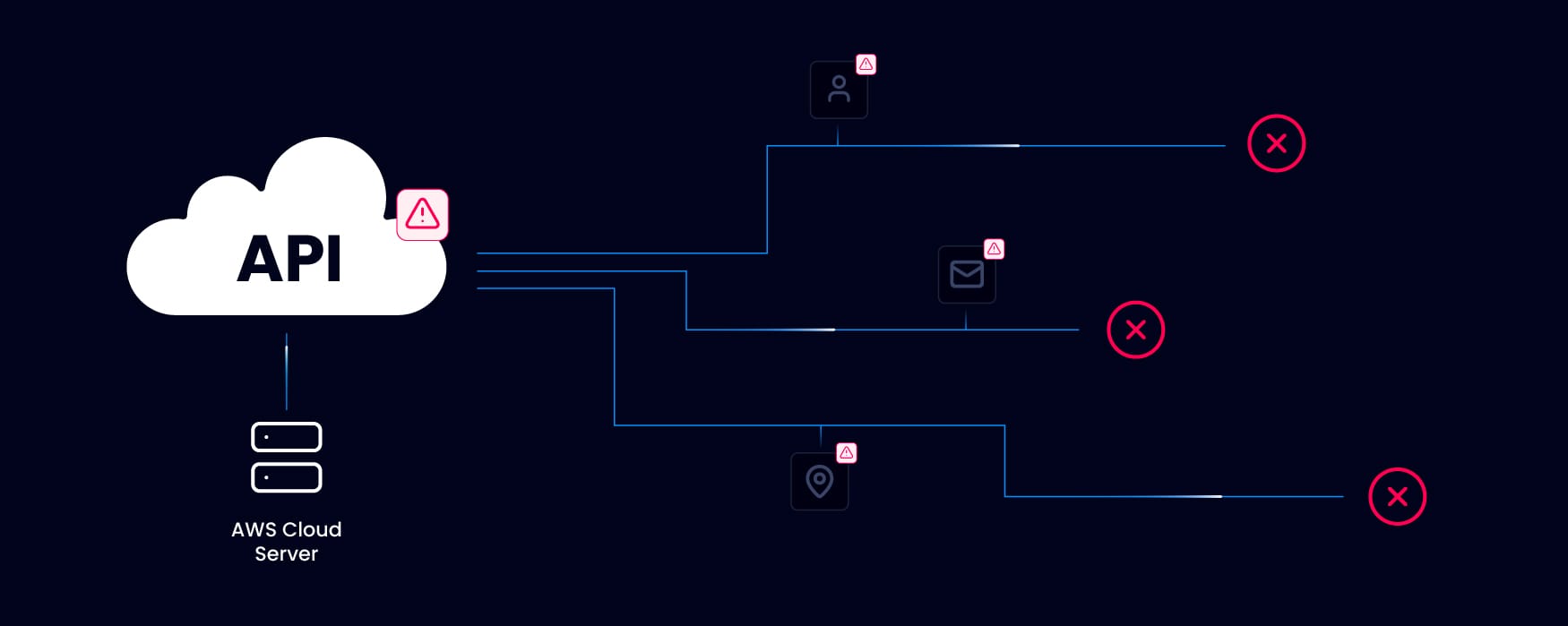
How a misconfigured API caused the Volkswagen data breach.
The VW data breach leaked some personal and sensitive data, including:
This level of exposure presented a unique risk: it enabled anyone with access to see where individuals lived, worked, and traveled, creating potential threats to their privacy and safety. The data could be used to predict daily routines, identify frequented locations, and even infer patterns about personal habits.
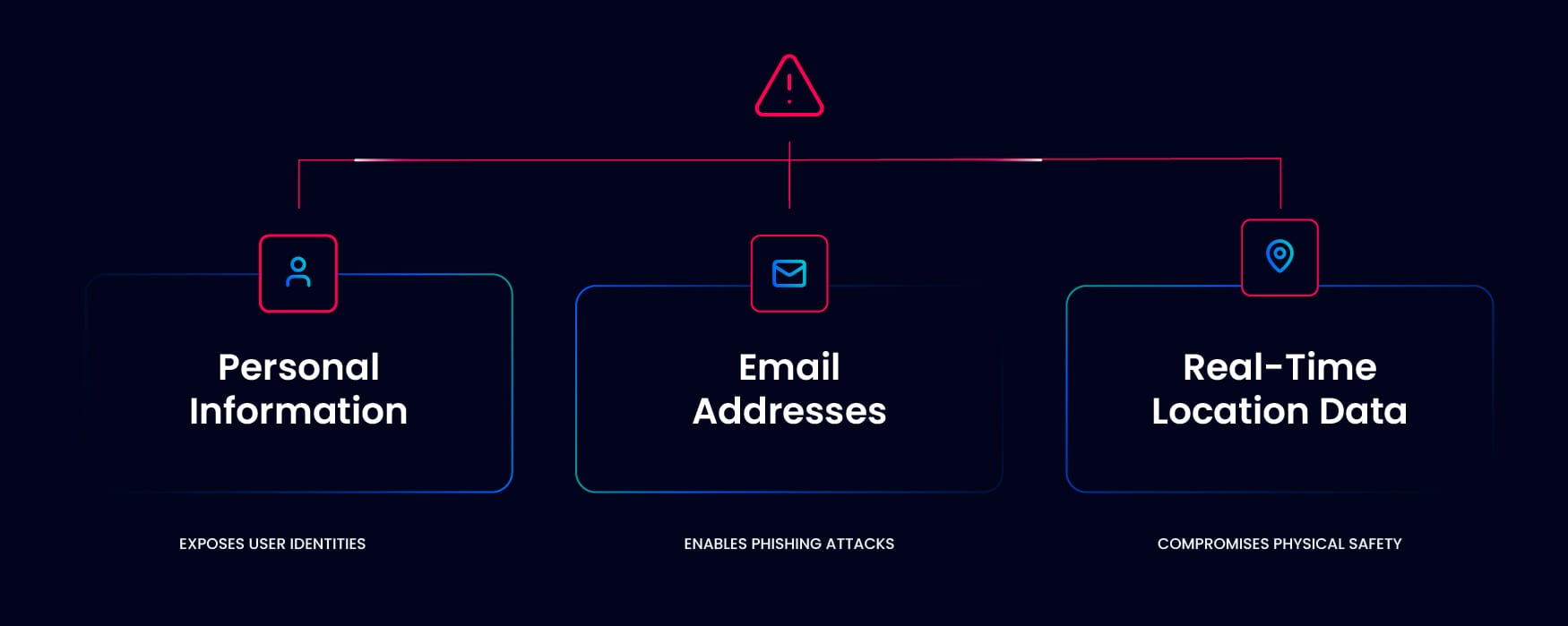
Sensitive data exposed: personal info, emails, and location data.
The Volkswagen API breach went beyond exposing generic user information. It exposed the risks of personal data collection, especially in an era of hyper-connectivity.
The Volkswagen app, a feature-rich platform designed to enhance the driving experience, was at the heart of this incident. The app offered functionalities like pre-heating the car on cold mornings, remotely locking and unlocking doors, and even locating the vehicle in a crowded parking lot.
For many, these features represented a seamless blend of technology and convenience, enabling drivers to interact with their vehicles like never before.
However, beneath the surface, the app also became a tool for transmitting sensitive data. Once users set up the app, their cars began collecting and sending information back to the AWS server, including:
For Nadja Weippert, a member of the German Bundestag, this breach revealed unsettling insights about how her personal data was being tracked and stored. After setting up the app, her vehicle recorded her parking locations and transmitted this information in real-time to Volkswagen’s servers.
The VW data breach exposed a trove of information, including Weippert's home address, frequented locations, and daily commute patterns.
The implications were severe for a public figure like her. Strangers or adversaries could easily identify where she lived and worked, posing serious privacy, security, and personal safety risks.
This breach wasn’t limited to Weippert. For hundreds of thousands of drivers, the exposed data represented more than an invasion of privacy; it posed tangible risks. Data sets like these can be weaponized in various ways:
For Markus Grübel, a CDU Bundestag member from Esslingen am Neckar, the VW data breach was a reminder of the vulnerabilities of digital tools. While these technologies offer convenience, they can inadvertently expose users to significant risks.
This breach is not an isolated case; it reflects patterns we have seen in other major API incidents, such as DotPe’s exposure to payment data and T-Mobile’s leak of sensitive customer records.
In each case, misconfigured APIs and a lack of proactive monitoring were the root causes, highlighting the dangers of insufficient API governance.
These examples underline an urgent call for organizations to adopt real-time observability and implement strong security practices to safeguard user data effectively.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Here are key learnings from the Volkswagen API breach to avoid the common API pitfalls:

Lessons learned: observability, compliance, minimization, and governance.
Treblle isn’t just another observability tool; it’s an API Intelligence platform. From development to production, Treblle simplifies API governance, enhances security, and ensures compliance without adding complexity to your workflows.
Here’s how we could have helped Volkswagen prevent the breach:
1. API Observability
Treblle tracks every API request for 40+ data points and displays it in a visually analyzable way, enabling immediate detection of unauthorized access or suspicious activity.
Treblle also performs detailed security checks on each API request, detailing the issues and their severity. This helps developers prioritize critical issues over others.
In the VW data breach case, such observability could have flagged the excessive transmission of location data, enabling the company to intervene before the breach occurred.
2. Compliance Checks
Security is at the core of Treblle’s platform, ensuring APIs are robust and compliant with privacy regulations like GDPR, CCPA, and PCI.
Treblle scans API responses to identify data that violates privacy regulations, such as unmasked location details or personal identifiers.
In the case of Volkswagen’s API breach, Treblle’s API Compliance check feature would have proactively flagged the exposure of sensitive personal data in real time. By identifying private details like unencrypted user information or improperly masked API responses, Treblle would have immediately alerted the development and security teams, allowing them to rectify the issue before it escalated.
3. Comprehensive Governance
API governance is critical for maintaining security. Treblle evaluates each API for its AI readiness, performance, design, and security against industry standards, giving developers a clear understanding of its current state and areas for improvement.
4. Traceability
Every API call, data access, and response is logged and traceable, making it easy to pinpoint the origin of unauthorized access.
Teams can quickly trace errors and security issues back to their source, reducing downtime and potential data exposure.
For an organization like Volkswagen, Treblle could have provided the clarity needed to swiftly track and address unauthorized API activity.
5. Custom Alerts and Role-based access
Treblle enables teams to set custom alerts, allowing for quick detection and response to potential breaches. These alerts are fully customizable, letting teams define specific thresholds, conditions, or incident types they want to monitor closely.
For instance, a sudden spike in API calls or unauthorized access attempts can trigger an immediate alert, ensuring suspicious activity is swiftly identified.
Treblle integrates with communication tools like Slack, directly delivering notifications about critical incidents to relevant inboxes or channels.
Additionally, Treblle provides role-based permissions, ensuring that only authorized users can access specific APIs or sensitive data.
Volkswagen Group could have prevented the API breach by limiting access to APIs containing and passing user data.
As APIs continue to drive digital transformation, organizations must recognize their dual-edged nature. Volkswagen’s breach highlights the cost of underestimating API security and serves as a roadmap for improvement.
By investing in API observability and governance tools like Treblle, organizations can:
In the fast-evolving digital landscape, proactive measures are not just recommended; they’re essential.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.