By industry
By initiatives
By industry
By initiatives
API Design | Aug 25, 2025 | 10 min read | By Savan Kharod | Reviewed by David Blažević

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
API headers are a fundamental part of how web services communicate, yet they’re often glossed over in documentation or misunderstood in practice. Whether you're building an API from scratch or integrating with third-party services, headers carry critical information that influences how your requests are handled and how responses are returned.
Transform APIs into a competitive advantage, download Innovation Through APIs for free.
This guide breaks down what API headers are, how they work in both requests and responses, and why you should pay attention to them. We'll also look at how tools like Treblle help make headers visible and actionable, so you’re not left guessing when something goes wrong.
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
Need real-time insight into how your APIs are used and performing?
Treblle helps you monitor, debug, and optimize every API request.
Explore Treblle
API headers are metadata, structured as key-value pairs, that accompany every HTTP request and response, supplying essential context beyond the body or URL. They sit between the request line/status and the body, providing directives, authentication data, and control instructions that guide how messages are interpreted and handled.
An HTTP message typically consists of:
A request line or status line
Zero or more header fields
An empty line
Optional message body (data payload)
Example:
GET /users HTTP/1.1
Host: api.example.com
Authorization: Bearer <token>
Accept: application/json
{ "unused": "in this example" }Headers define how requests are processed, including the format, authentication context, caching behavior, and other related details.
URL parameters (path/query) define which resource is being accessed.
The body contains the actual payload for operations like POST or PUT.
The clarity provided by headers ensures APIs function predictably, securely, and efficiently.
In the following sections, we’ll explore how request headers give context to API calls, how response headers shape behavior and performance, and why authorization headers require careful handling.
When a client makes an API call, it doesn’t just send the URL and payload; the request headers carry essential context that tells the server how to process that call. Proper use of request headers ensures APIs behave predictably, handle data correctly, and enforce security.
Define payload format: The server uses headers to determine how to parse the body (e.g., JSON, XML, form data).
Negotiate content: Clients can express what response formats they accept.
Authenticate and authorize: Credentials and tokens travel in headers, keeping sensitive data out of URLs.
Identify clients: Headers reveal client details (version, platform), which aids in analytics and troubleshooting.
Custom metadata, such as tracing IDs or feature flags, can be passed using bespoke headers tailored to your application's unique requirements.
Specifies the media type of the request body. The server uses this to select the correct parser.
Content-Type: application/jsonIf you’re sending JSON, XML, or URL‑encoded form data, setting this header is mandatory for proper handling.
Indicates which media types the client can process in the response. The server may use this to perform content negotiation.
Accept: application/json, text/plain;q=0.8Clients can rank preferences using quality factors (the q parameter).
Carries authentication credentials. Common schemes include:
Authorization: Bearer eyJhbGciOi...Authorization: ApiKey 12345abcdeAuthorization: Basic dXNlcjpwYXNzd29yZA==Identifies the client application, library, or device making the request. Servers often log this for monitoring or adapt behavior based on client capabilities.
User-Agent: MyApp/1.2.3 (iOS; en_US)When standard headers aren’t enough, you can define your own. Common examples include:
X-Request-ID: Carries a unique identifier for tracing distributed requests.
X-Feature-Flag: Toggles experimental features per request.
X-Tenant-ID: Indicates the customer or organizational context in multi‑tenant APIs.
X-Request-ID: 9f1b3c2a-6d4e-4f7b-9a8d-1234567890abMost frameworks expose headers as a simple dictionary or map. For example purposes, we will be using the three most popular frameworks:
app.post('/data', (req, res) => {
const contentType = req.get('Content-Type');
const token = req.get('Authorization');
// ...
});from flask import request
@app.route('/data', methods=['POST'])
def data():
content_type = request.headers.get('Content-Type')
api_key = request.headers.get('X-API-Key')
# ...[HttpPost("data")]
public IActionResult PostData()
{
var contentType = Request.Headers["Content-Type"].ToString();
var userAgent = Request.Headers["User-Agent"].ToString();
// ...
}By understanding and correctly leveraging request headers, you ensure your API calls carry the full context needed for robust, secure, and efficient processing.
In HTTP API communication, response headers carry metadata from the server back to the client, controlling how payloads are interpreted, cached, secured, and how clients should proceed.
Common response headers include Content-Type, Cache-Control, Set-Cookie, RateLimit-*, and CORS-related headers, such as Access-Control-Allow-Origin, each playing a specific role in content negotiation, caching protocols, session management, rate limiting, and cross-origin resource sharing.
Response headers provide instructions and context about the server’s response, separate from the message body. They tell the client how to parse the payload, whether and how to cache it, how to handle cookies, the client’s rate limit status, and whether cross‑origin requests are permitted.
The Content-Type header indicates the media type of the response body, enabling the client to select the correct parser (e.g., JSON, XML, HTML).
The Cache-Control header holds directives that control caching in browsers and intermediate proxies, such as no-store, max-age, and public, to manage freshness and performance.
The Set-Cookie header enables the server to send cookies to the client, which the client stores and returns in subsequent requests for session management or personalization purposes. Cookies can include attributes such as Max-Age, HttpOnly, and Secure to enhance security and control their lifetime.
Rate-limit headers, such as RateLimit-Limit, RateLimit-Remaining, and RateLimit-Reset, inform the client of its current request quota and when it will be reset, helping to prevent throttling and manage request pacing effectively. Properly implementing and observing these headers lets clients back off when necessary and avoid HTTP 429 responses.
Cross-Origin Resource Sharing (CORS) headers, such as Access-Control-Allow-Origin, specify which origins can access the response, ensuring that browser security models enforce the intended resource-sharing policy. Additional CORS headers, such as Access-Control-Allow-Methods and Access-Control-Allow-Headers, define the permitted methods and headers for preflight requests, enabling secure cross-domain interactions.
The ETag header provides a unique identifier for a specific version of a resource, enabling efficient cache validation and conditional requests (If-None-Match) to reduce bandwidth usage.
When a client exceeds its rate limit, the Retry-After header may indicate how many seconds to wait before making a new request, guiding automated backoff strategies.
Authorization headers are HTTP headers used to transmit security credentials with every API request, enabling servers to authenticate and authorize client access before processing calls. They keep sensitive credentials out of URLs and request bodies, thereby reducing exposure in logs and browser histories. Common schemes include Basic, Bearer, and API Key authentication, each defined by its own format and use case :
Basic Auth encodes a username:password pair in Base64, as specified by RFC 7617, and should only be used over HTTPS due to its simplicity and lack of inherent encryption.
Bearer tokens follow the OAuth 2.0 spec (RFC 6750), where the token itself grants access to resources without exposing account credentials.
API Keys can be transmitted in the Authorization header using a custom prefix (e.g., ApiKey) or alongside Bearer authentication, offering straightforward implementation for service-to-service calls.
Other schemes, such as Digest or custom token formats, are also supported by modern clients and servers, as documented by Beeceptor’s HTTP authorization overview.
Because authorization headers carry highly sensitive information, always use HTTPS to secure them in transit and never log their full values. Apply robust authorization logic per the OWASP Authorization Cheat Sheet to ensure that header-based credentials map correctly to permissions and roles.
Misconfigured CORS policies can inadvertently expose Authorization headers to unauthorized origins, so define strict Access-Control-Allow-Origin rules and preflight checks. Tools like Treblle capture and mask authorization headers in real time, providing visibility into header usage without risking credential leaks, making it easier to debug authentication issues and audit security posture.
Effective header management is essential, but headers often reside outside your main business logic. Treblle provides complete visibility into both request and response headers, making debugging and auditing easy without requiring access to logs or guesswork.
With Treblle's SDK installed (Node.js, Flask, .NET, etc.), every request and response, including all headers, is sent securely to your Treblle dashboard. Treblle logs Content-Type, Authorization, CORS-related headers, custom metadata, and rate-limit values without manual instrumentation.
The Treblle dashboard provides a Recent Requests view where you can inspect headers for each API call. Select a request to view both request headers and response headers side by side, along with timing and status code, enabling fast troubleshooting when integration fails or headers look wrong.
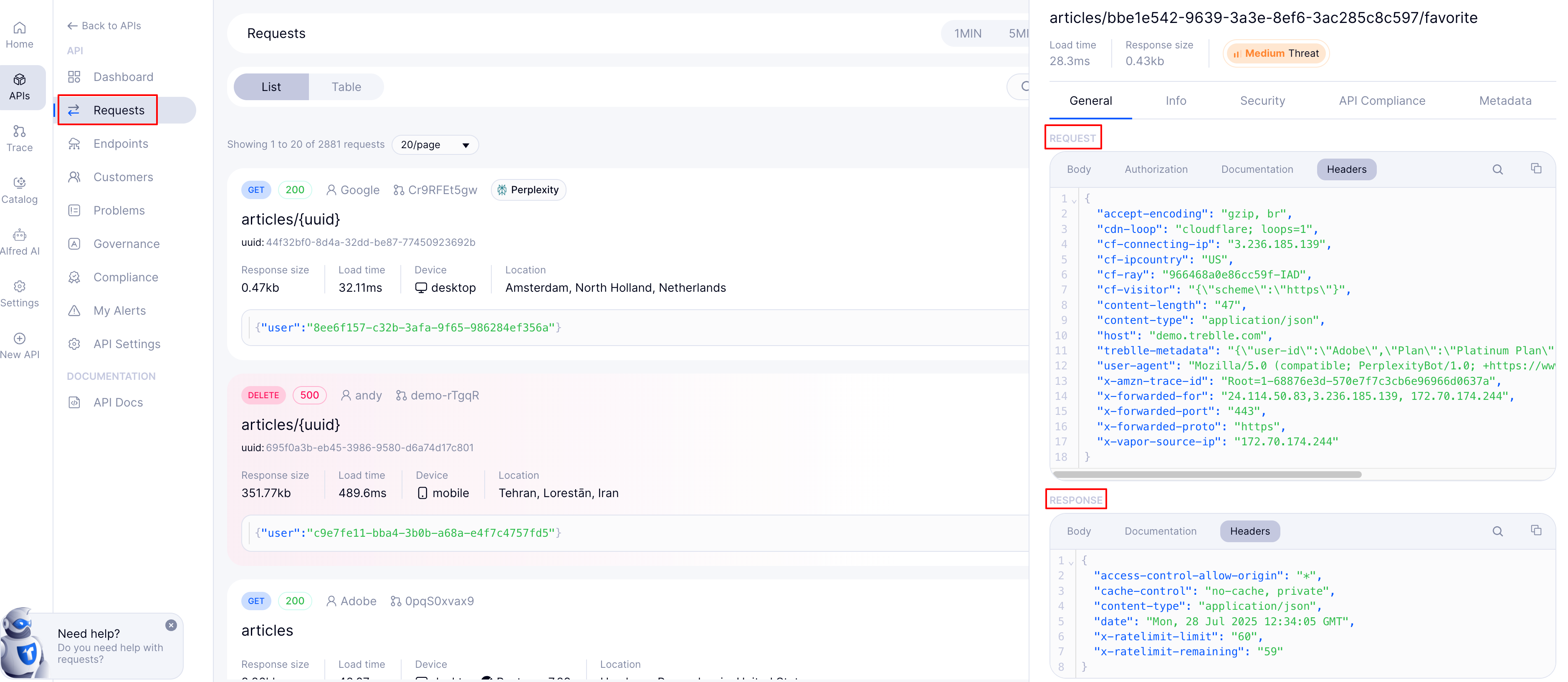
If a 401 Unauthorized error occurs, review the Authorization header directly in Treblle. Validate the token format and expiry, and ensure the header is included. Treblle masks sensitive values but lets you see presence and structure intact.
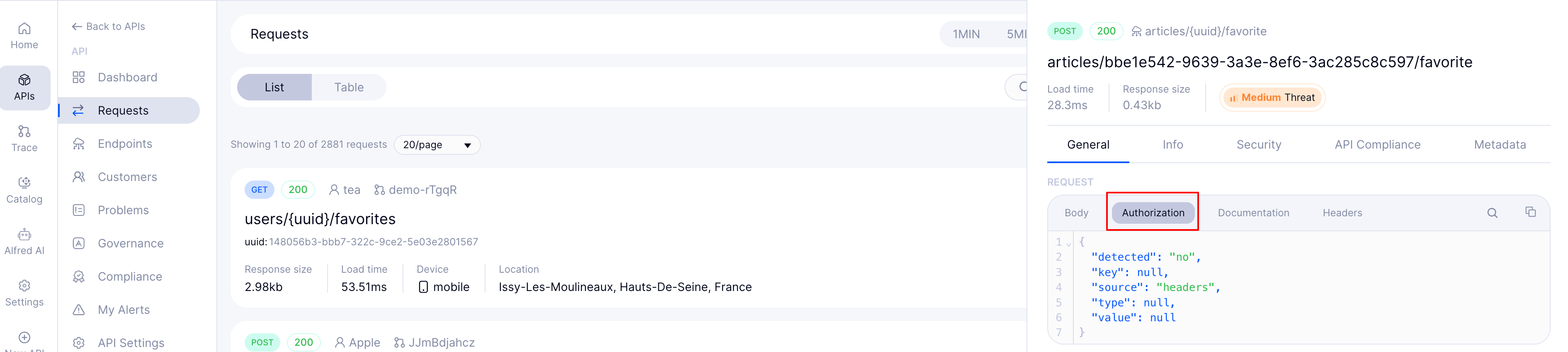
Identify issues such as missing Content-Type, incorrect Accept headers, or missing CORS headers. Treblle displays all header fields so that you can promptly identify missing or malformed values.
Treblle automatically hides sensitive header values (like Authorization) while still allowing you to confirm their presence and basic structure. This supports compliance and avoids exposing secrets during audits or debugging sessions.
Treblle combines header data with performance metrics, error traces, and governance insights. For example, if a client hits rate limits, Treblle surfaces RateLimit-* headers alongside response time and error logs, making it easy to correlate behavior with header semantics. You can also trace custom header values such as treblle-user-id to individual user sessions across requests.
See how your APIs are adopted and used with clean, actionable data.
Treblle gives you dashboards and insights built for APIs.
Explore Treblle
See how your APIs are adopted and used with clean, actionable data.
Treblle gives you dashboards and insights built for APIs.
Explore Treblle
Understanding API headers is a foundational step toward building more predictable, secure, and resilient API integrations. These small pieces of metadata carry out critical responsibilities, such as content negotiation, authentication, rate limiting, and caching.
Effective API development means treating headers as first-class citizens, not afterthoughts. Treblle enhances this approach by automatically capturing all header data (while masking sensitive values), allowing you to see exactly what headers were sent and received for each API transaction.
Treblle’s dashboards correlate header insights with errors, latency, rate-limit hits, and security alerts, turning header management into actionable observability.
 API Design
API DesignDiscover the 13 best OpenAPI documentation tools for 2026. Compare top platforms like Treblle, Swagger, and Redocly to improve your DX, eliminate documentation drift, and automate your API reference.
 API Design
API DesignAPI authorization defines what an authenticated user or client can do inside your system. This guide explains authorization vs authentication, breaks down RBAC, ABAC, and OAuth scopes, and shows how to implement simple, reliable access control in REST APIs without cluttering your codebase.
 API Design
API DesignRate limiting sets hard caps on how many requests a client can make; throttling shapes how fast requests are processed. This guide defines both, shows when to use each, and covers best practices.