API Security | Sep 3, 2025 | 9 min read | By Rahul Khinchi | Reviewed by Savan Kharod

Rahul Khinchi is a Developer Advocate at Treblle, where he focuses on improving API workflows and developer experience. He writes technical content on API observability, security, and governance, and builds open-source tools to demonstrate real-world API use cases. Rahul has spoken at developer meetups and universities, and previously held developer advocacy roles at Syncloop. He was selected for Google Summer of Code in 2022 and has led community initiatives supporting thousands of beginners in open source.
There’s always that one endpoint that shows up in production and makes everyone say, "Wait, who added this?"
It’s not in the docs. It’s not in the OpenAPI file. Nobody wants to take ownership.
You grep the codebase, dig through old PRs, and eventually find it buried in a test script someone forgot to remove three sprints ago.
That’s a Shadow API.
They happen more often than you’d think, especially when product teams are shipping fast, and QA is cutting corners with debug routes. It’s more than just about security; it's about knowing what’s actually running in your environment.
In this blog post, we will look at the top tools teams use to catch Shadow APIs, how they work, where they fall short, and how Treblle approaches the same problem differently from a developer's point of view.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Shadow APIs include any endpoints running in your environment that your team doesn't know about. Your OpenAPI spec doesn't track them.
They’re not in your developer portal. No one wrote tests for them. But they’re live, and they’re getting traffic.
They appear in several ways: a developer quickly patches a bug by creating a new endpoint, a microservice exposes an internal API that accidentally becomes externally accessible, or a third-party integration creates endpoints you never documented.
If you want to dive deeper into how shadow APIs differ from zombie APIs, this article on Zombie APIs vs Shadow APIs: What’s the Difference?, offers a great breakdown, covering definitions, real‑world cases, mitigation strategies, and tooling approaches.
In 2023, researchers uncovered an undocumented internal endpoint used by T-Mobile for mobile app diagnostics. This endpoint wasn’t listed in any public API reference and lacked proper authentication checks.
As a result, anyone who discovered it could pull sensitive customer data simply by supplying a device identifier.
What makes this case striking is how it slipped through into production. It began as a debug endpoint to troubleshoot the mobile app. Developers forgot to remove it, and it remained accessible, untracked by inventory tools or API gateways.
Threat actors eventually found it through automated discovery techniques, including endpoint fuzzing and proxy analysis.
Shadow APIs create three critical problems.
First, they expose attack surfaces you cannot defend because you do not know they exist.
Second, they violate compliance requirements when they handle regulated data without proper controls.
Third, they create maintenance chaos when these undocumented endpoints break, and nobody knows how to fix them or which systems depend on them.
Effective shadow API detection requires four capabilities: real-time visibility into all API traffic, automatic discovery of new endpoints, contextual metadata about each API's source and purpose, and alerting systems that notify you when new APIs appear.
So, what should you look for in a tool that claims to detect them?
Real-time visibility: You should see requests as they happen. Not batched logs an hour later.
API discovery: The tool needs to automatically surface new or unknown endpoints, not just inspect traffic from known paths.
Contextual metadata: Knowing an endpoint exists doesn't provide enough information. You need to know where it originated, what someone called it, and who made the request.
Alerting and historical tracking: If something new pops up or changes behavior, you should hear about it. And be able to review it later.
Let’s look at a few tools that claim to solve this and how they compare.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
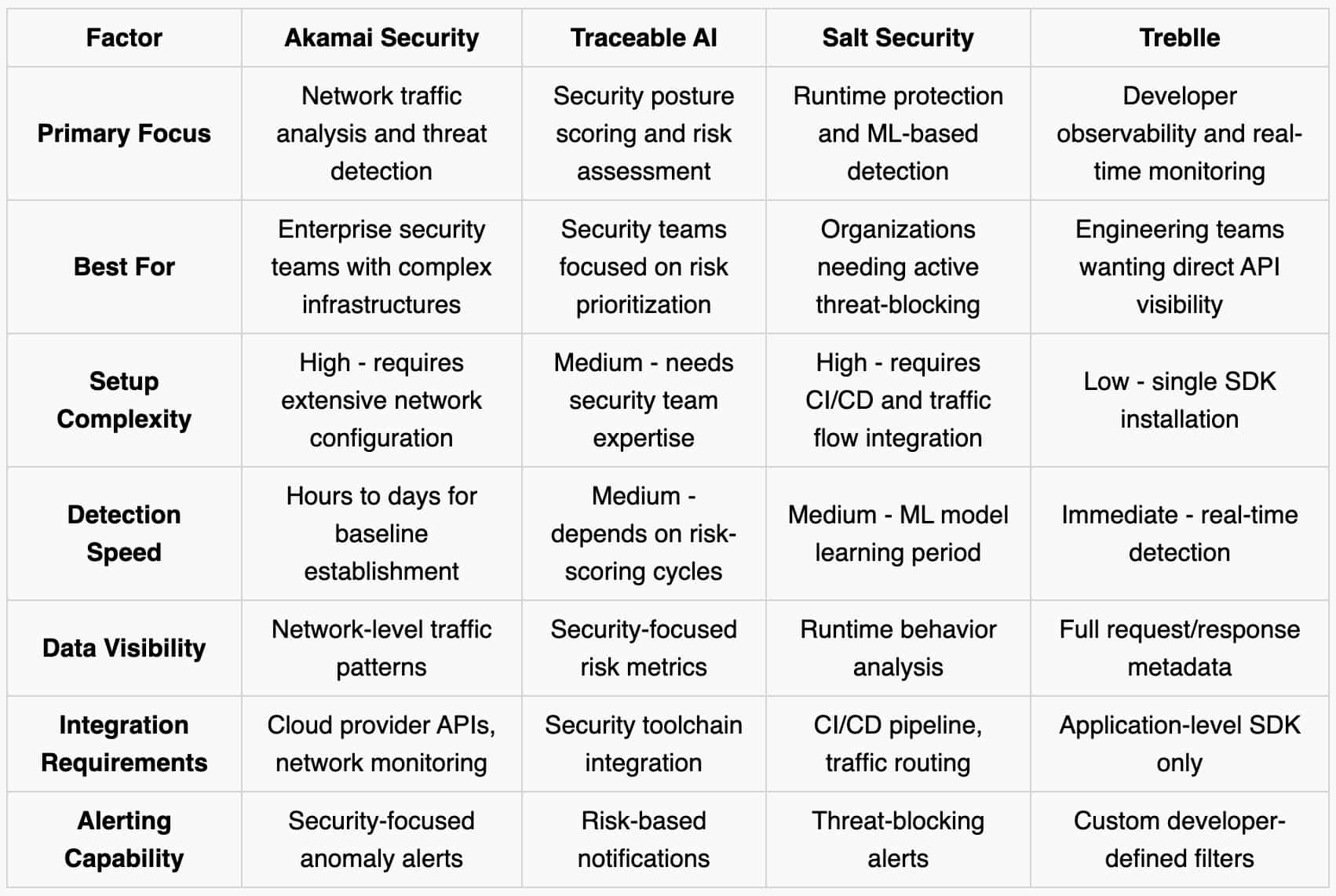
Akamai Security analyzes network traffic to identify API endpoints. The platform examines HTTP and HTTPS traffic flowing through your infrastructure, using machine learning to baseline normal API behavior and flag anomalies.
Strengths:
You get a high-fidelity traffic map. Akamai analyzes the payloads, headers, and even rate patterns.
Their anomaly detection flags unexpected API behavior, such as strange query patterns or unknown sources.
They integrate well with enterprise environments like AWS, Azure, and GCP.
Limitations:
The platform targets security teams, not developers. Setup consumes time. You must deploy collectors, configure mirrors, and tune the alerts.
Enterprise contracts gate most features. The cost and complexity may lock you out if you run a lean startup or mid-sized engineering team.
Traceable AI approaches shadow API detection through security posture scoring. The platform assigns risk scores to API endpoints based on their behavior, data sensitivity, and security controls.
Strengths:
You can monitor behavioral changes in APIs. The system notifies you if an endpoint receives new payload shapes or requests from a new region.
The scoring system helps prioritize which APIs need attention based on threat models.
Their risk reporting is thorough and can feed directly into security review cycles.
Limitations:
The platform targets security and compliance teams. Developers trying to trace where a new API originated may find it too abstract.
Discovery isn't its core strength. It’s better at telling you which APIs are acting weird than surfacing ones you didn’t know existed.
Salt Security uses machine learning to identify "zombie" and shadow APIs by analyzing runtime traffic patterns. The platform learns your standard API usage patterns and flags endpoints that do not match established baselines.
Strengths:
Their detection of deprecated or forgotten APIs is solid. If something hasn’t been touched in a while but still receives traffic, it gets flagged.
They provide runtime protection and integrate well with CI/CD pipelines for continuous security monitoring.
Limitations:
Developer visibility is limited. You get alerts but not the full request/response breakdown in a developer-friendly format.
It works best when fully integrated into your entire stack. If you miss one ingress path or your CI/CD process is loosely defined, you'll get gaps.
But if you’re a developer looking for instant visibility, minimal setup, and full request context, these platforms may fall short.
Now, we will see how Treblle approaches shadow API detection differently from traditional security-focused tools.
Treblle streams every API request live into its dashboard without waiting or batch processing.
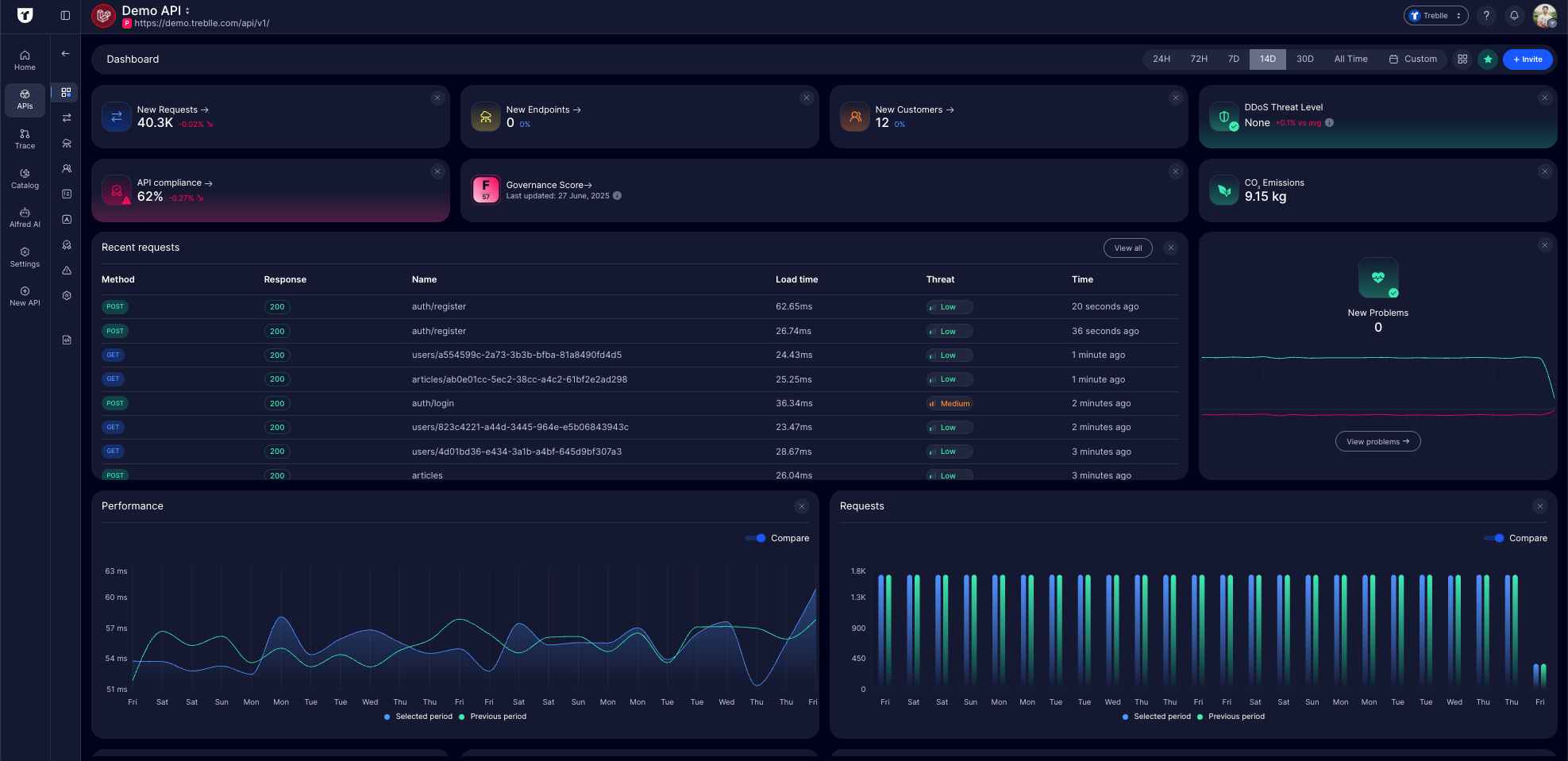
Your service appears in the dashboard as soon as a call is received.
Endpoints not appearing in your OpenAPI spec or documentation are "unknown," and you can immediately inspect them. Integration requires just one SDK that auto-detects endpoints as they receive traffic, with no manual configuration needed.
Consider a scenario where your mobile app team adds a new /api/user/preferences endpoint to handle notification settings.
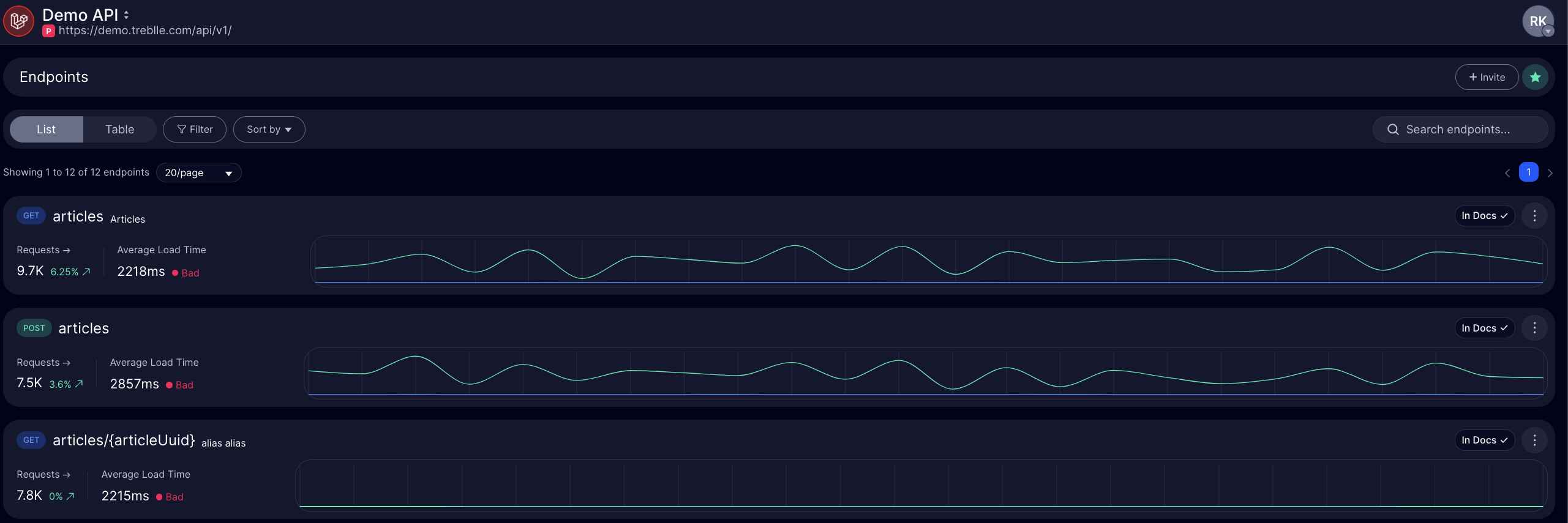
Treblle shows you the endpoint the moment the first mobile client hits it, along with the request structure and response format. This immediate detection happens because Treblle sits at the application layer, not the network layer.
Instead of analyzing traffic patterns to infer API behavior, Treblle directly observes what your application code executes.
Treblle captures comprehensive information for each incoming request, including client IP, headers used, full payload and response body, the API version or route invoked, response time, status code, size, and more than 120 data points.
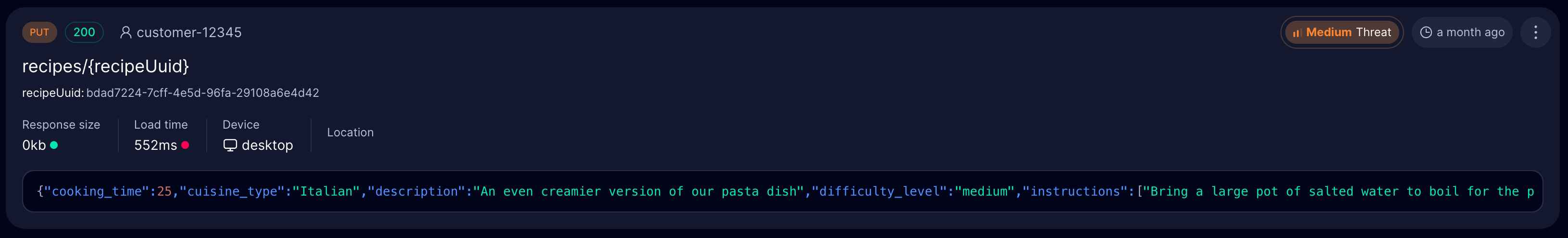
This metadata helps you track down the source of a stray endpoint, link it to a specific feature branch or test script, and reconstruct the full context of the call without hunting through raw logs.
With Treblle 3.0's custom alerts, you can define filters based on criteria like calls to undocumented endpoints, requests from unknown IPs, or authentication failures on new routes. Once you save your filter, Treblle sends alerts via email, Slack, or in-app notifications when it finds matches.
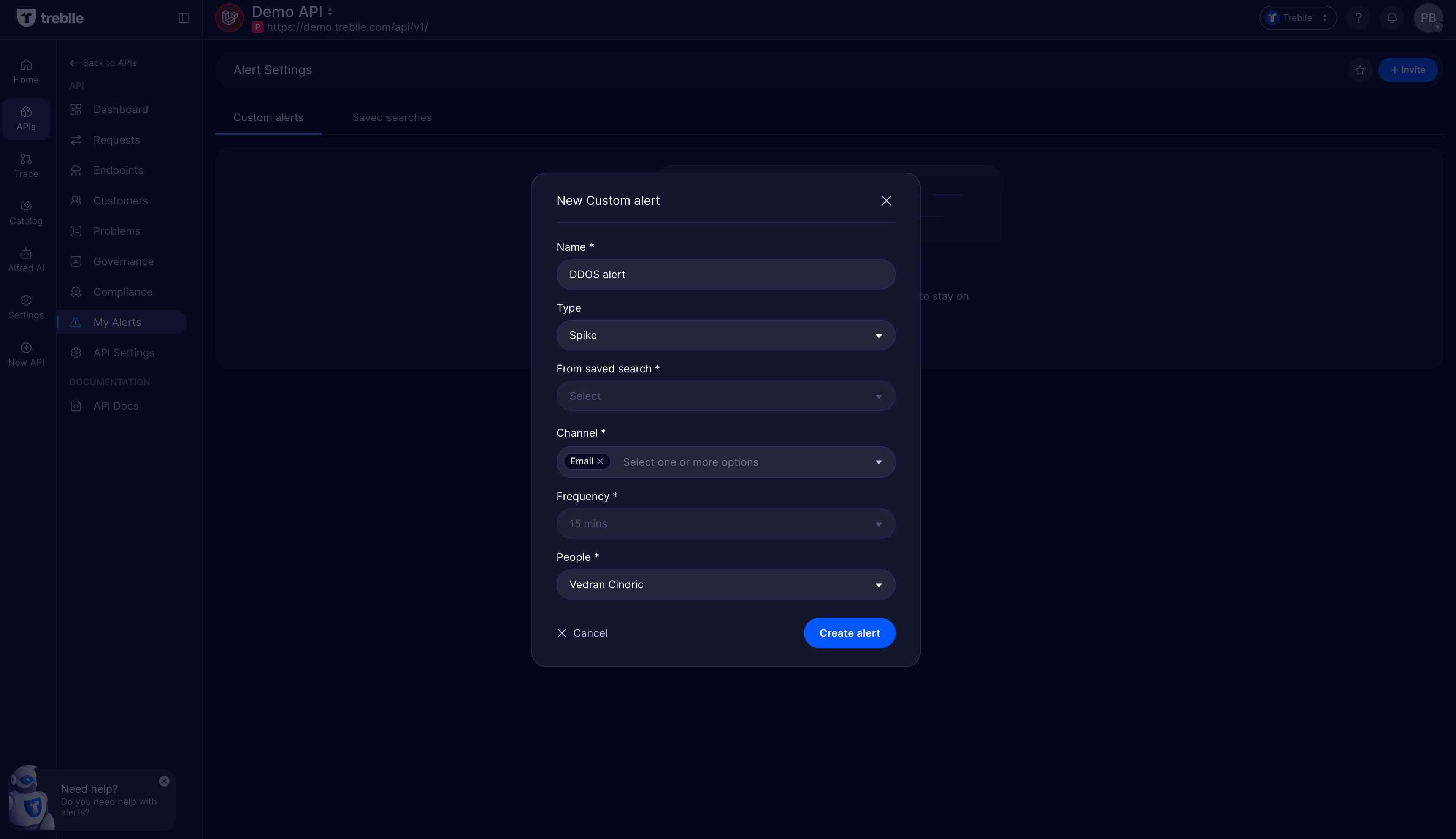
For instance, you might create an alert for any new endpoint containing "admin" or "debug" in the path. When a developer accidentally deploys a debug endpoint, you receive immediate notification rather than discovering it during your following security review.
You can also alert on geographic anomalies. If your API typically serves users in North America and Europe, you can get alerts when requests start coming from unexpected regions, potentially indicating API abuse or unauthorized access.
Unlike many shadow API tools that target InfoSec or audit teams, developers designed Treblle with their needs in mind. The integration stays simple (install the SDK, and it "just works"), the dashboard remains light and intuitive, and the surfaced data maps directly to the code-level activity. It shows you what runs, not what should run.
When you deploy new code, Treblle shows which new endpoints appeared, what data they handle, and how clients use them, This visibility helps developers catch unintended API exposure before it becomes a security issue.
For a real-world example of how visibility could have prevented a major API breach, see this breakdown of the Volkswagen API incident.
The system stores every API transaction in a searchable history. To replay a request or recreate an incident, you can filter on any field, including time range, headers, status codes, and query parameters.
Treblle's dashboard puts contextual data at your fingertips, reducing the time spent decoding logs.
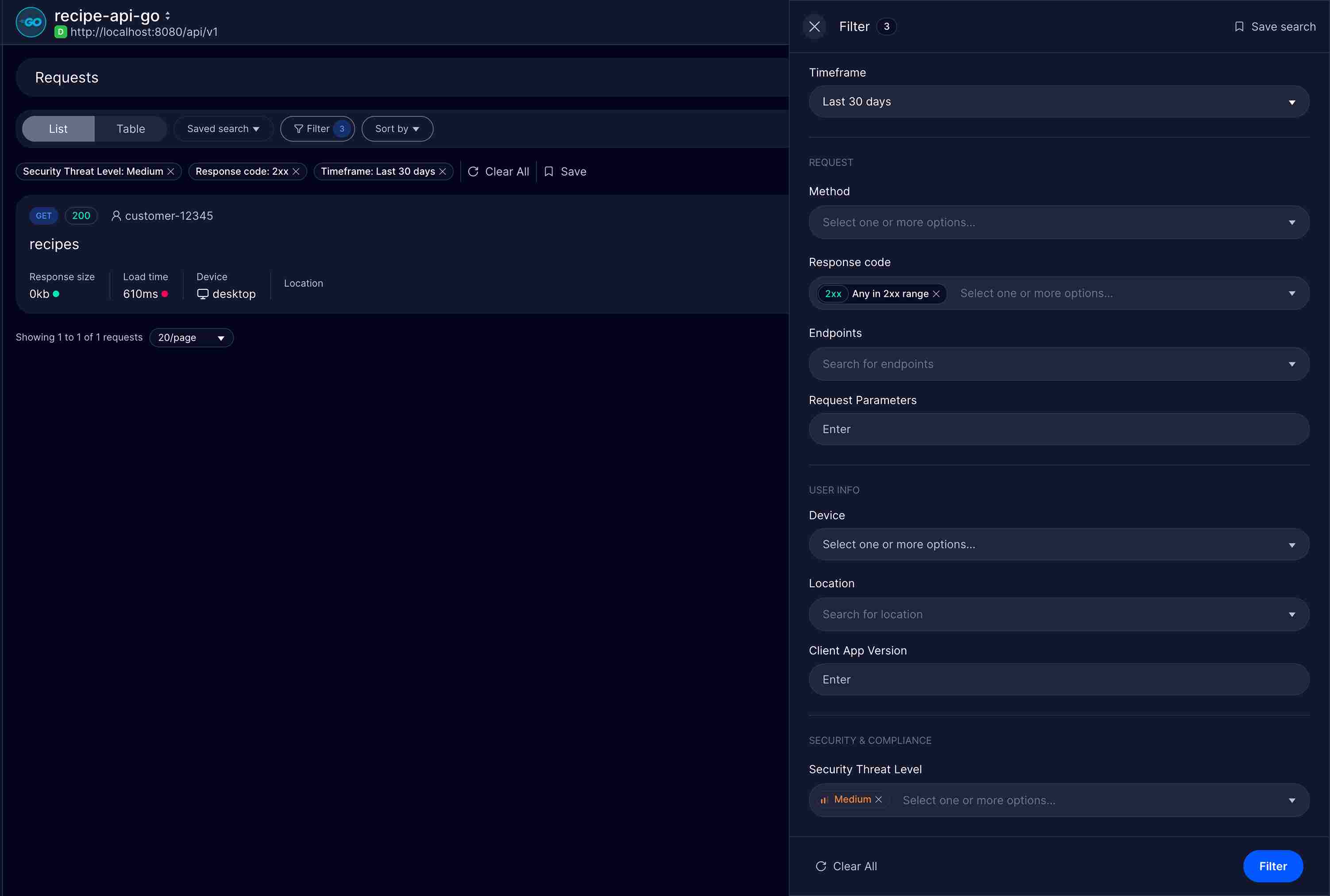
This historical data proves valuable during post-incident analysis. When investigating a data breach, you can search for all requests to sensitive endpoints during the suspected timeframe, identify the source of unauthorized access, and demonstrate the scope of the incident to auditors.
The search functionality supports complex queries. You can search for all 500 errors from a specific user-agent during a particular time window or find all requests to endpoints containing personal data that returned successfully without proper authentication headers.
Shadow APIs represent more than a security problem.
They indicate a gap between what you think your system does and what it actually does. Traditional security tools help you find and protect against threats but do not necessarily help you understand your API surface.
Effective shadow API detection requires tools that show you reality, not just what your OpenAPI specifications document. You need visibility into every request your application handles, context about where those requests originate, and the ability to trace new APIs back to their source code.
Treblle provides this visibility by sitting directly in your application stack and capturing comprehensive data about every API interaction as it happens.
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
Protect your APIs from threats with real-time security checks.
Treblle scans every request and alerts you to potential risks.
Explore Treblle
 API Security
API SecurityMoltbook launched in Jan 2026 without a basic API security hygiene...
 API Security
API SecurityAn Instagram data breach exposed 17.5 million users to scammers. Treblle explains what went wrong, how Instagram responded, and key prevention lessons.
 API Security
API SecurityOAuth 2.0 for APIs is how modern apps delegate access safely. This guide walks through the main flows, access vs refresh tokens, scopes, and the common mistakes that break real implementations.